SeeTestAutomation- iOS Profile Management and Creating Certificates And Provision Profiles
Please note that this tool is classified as a Legacy tool. We recommend transitioning to our updated solutions to maintain optimal performance and security in your workflows. For more information on this matter, please reach out to technical support .
This section explains how to create certificates, provision profiles, p12 files, and a developer profile (.developerprofile) that our products can work with.
These are used in the iOS profile management.
- Create an Apple Certificate
- Create a Provision Profile
- Create a Developer Profile or Create a .p12 file
In order to get to the iOS profile management:
-
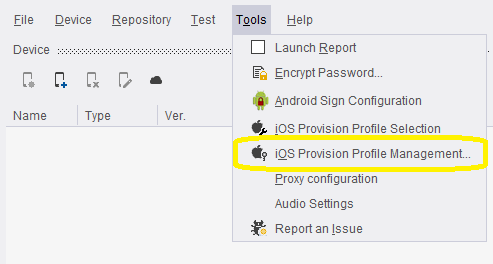
Click Tools → iOS Provision Profile Management.
-
Click Import from Apple developer account.

-
Export the Apple Developer Account file (.developerprofile).

-
Upload it
-
Enter the file's password. The file contains several signing identities and provision profiles, choose the combination to work with.
-
Generate the Certificate file (.p12) and Apple provision profile (.mobileprovision).
-
Enter certificate's password, then click OK.

Troubleshooting
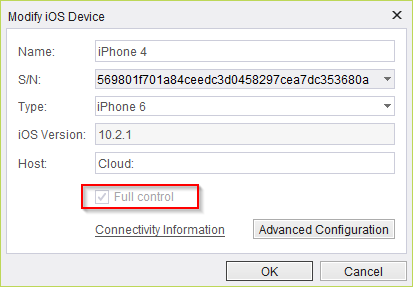
When adding a device, if 'Full control' is checked it means the device has a valid matching profile.
In a case where the device does not open, look for the following exceptions on a log.
Signing Identity Profile Not Found
When working on a Mac your Keychain must contain the iPhone developer certificate which is used from Digital.ai Testing. The certificate will be on the Login user and must have its private key. If it isn't there, import to your keychain the .p12 file for this certificate.
Apple Worldwide Developer Relations Certification Authority Doesn't Exist
When working on a Mac your Keychain must contain this certificate. The certificate will be on the System user.
Wrong Trust Settings for Apple Worldwide Developer Relations Certification Authority
Change the trust settings to use the system default.
All signing identities on Keychain need to have the trust setting 'Use system default'.