SonarQube Container Plugin
The SonarQube container plugin allows you to perform security scans and analysis of your code quality. SonarQube is installed and hosted on your own servers.
note
In the release flow editor, Container tasks have a red border.
Prerequisites
- Sonar server running and accessible via HTTP(s)
- Remote runner setup to run the container tasks
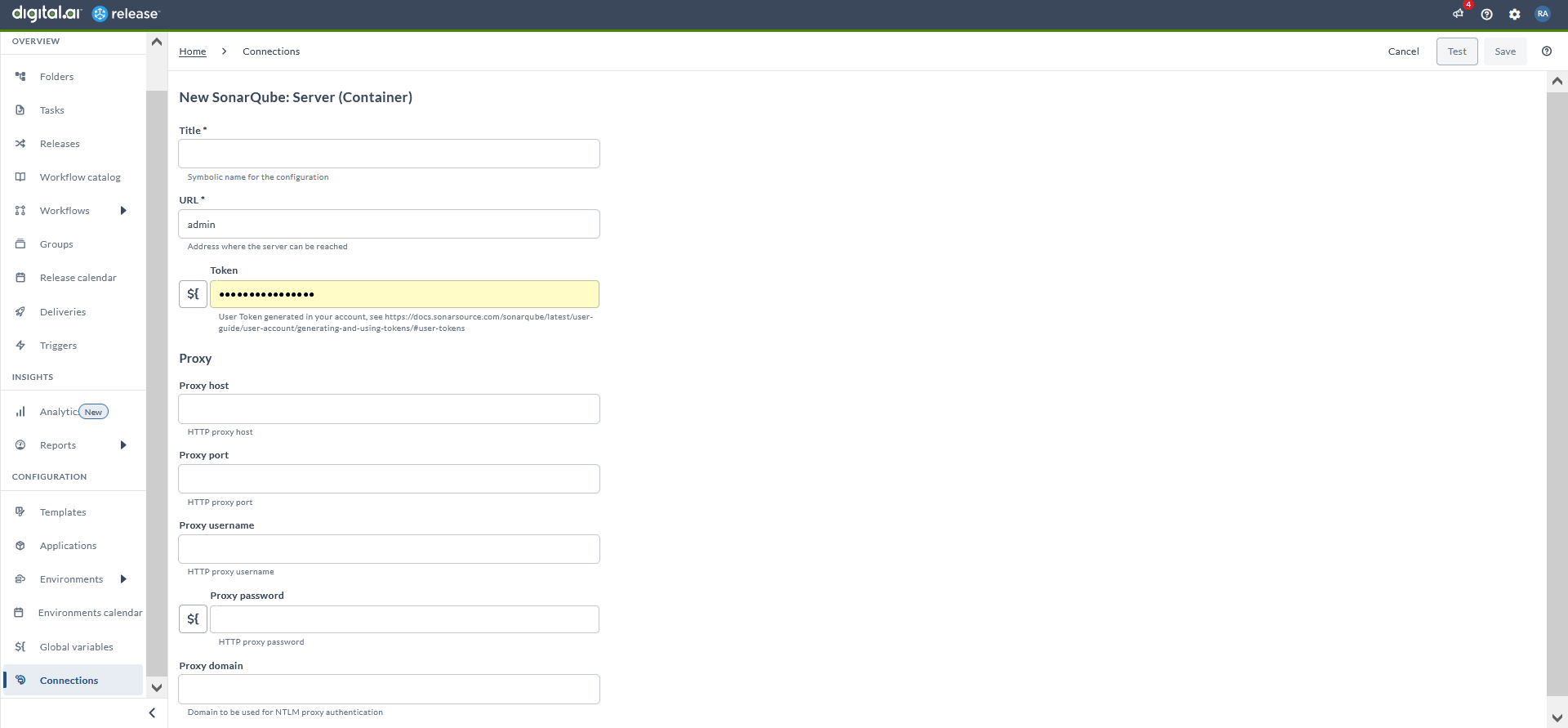
Set up Connection to Sonar Server
- From the navigation pane, under CONFIGURATION, click Connections.
- Under HTTP server connections, next to SonarQube: Server (Container), click
. The New SonarQube: Server (Container) page opens.
- In the Title field, enter the name of the configuration. This name will display in SonarQube tasks.
- In the URL field, enter the URL to access the server.
- In the Token field, enter the user token.
- If required, enter the proxy details.
- To test the connection, click Test.
- To save the configuration, click Save.
Note: Branch and Pull request fields are not mandatory.
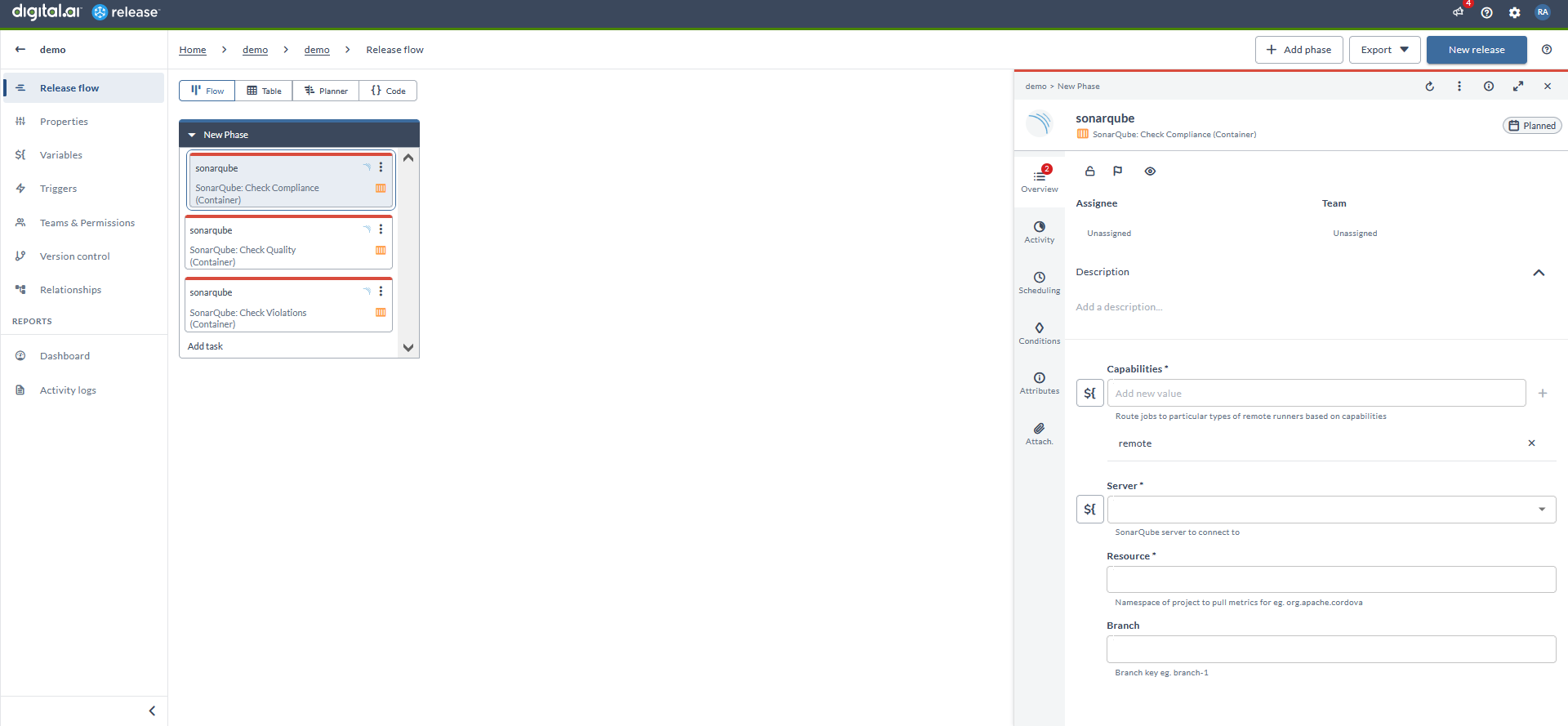
Check Compliance (Container)
- In the release flow tab of a Release template, add a task of type SonarQube > Check Compliance (Container).
- Click the added task to open it.
- In the Capabilities field, enter a value that matches the capability set for your Runner. This helps you to route jobs to that particular Runner.
- In the Server field, select the configured server.
- In the Resource field, enter the namespace of the project to pull the metrics.
- In the Branch field, enter the name of the GIT branch.
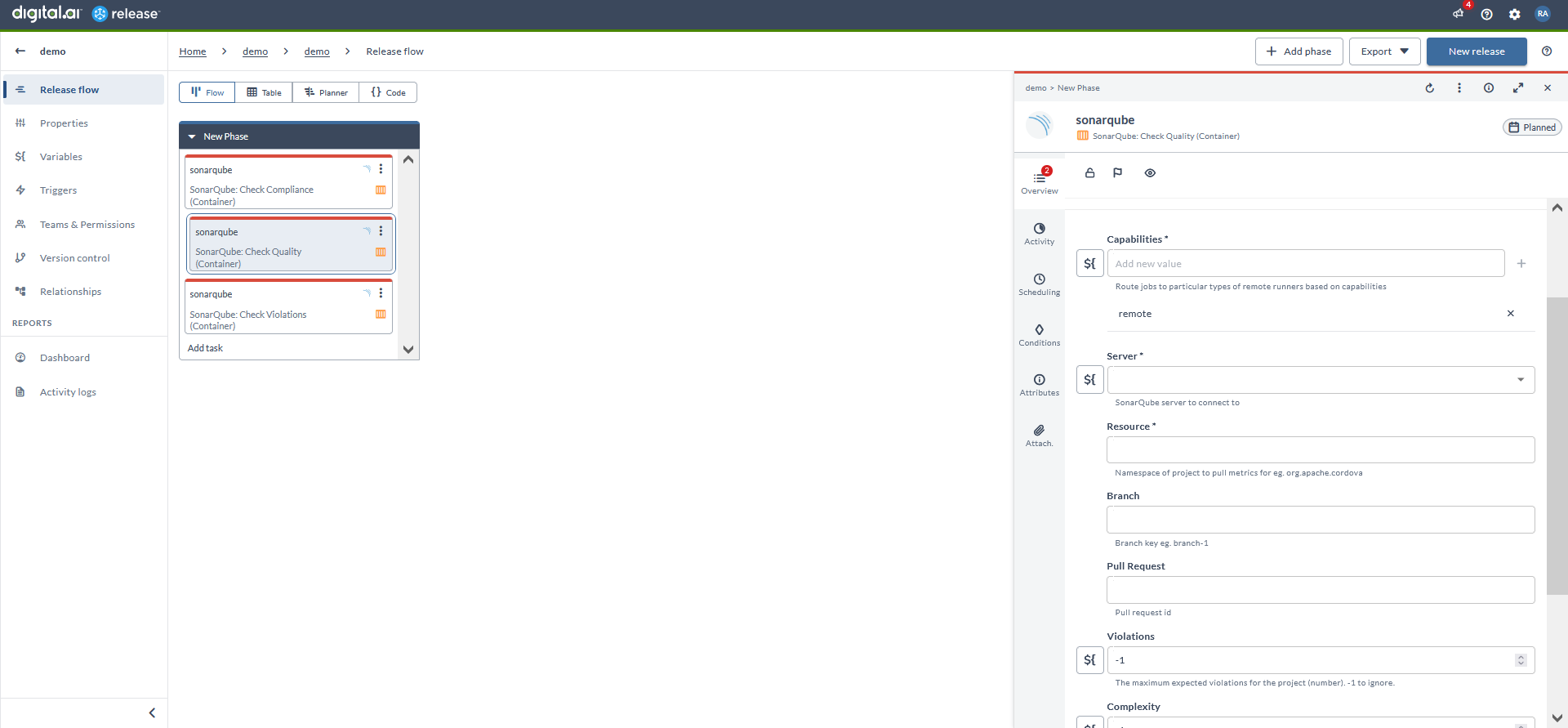
Check Quality (Container)
- In the release flow tab of a Release template, add a task of type SonarQube > Check Quality (Container).
- Click the added task to open it.
- In the Capabilities field, enter a value that matches the capability set for your Runner. This helps you to route jobs to that particular Runner.
- In the Server field, select the configured server.
- In the Resource field, enter the namespace of the project to pull the metrics.
- In the Branch field, enter the name of the GIT branch.
- In the Pull request field, enter the ID of the pull request.
Note: Enter
-1to ignore the following actions.
- In the Violations field, enter a number to define the maximum number of expected violations for the project.
- In the Complexity field, enter a number to define the maximum expected complexity for the project.
- In the Line Coverage field, enter a number to define the minimum expected line coverage for the project. The value must be in percentage.
- In the Duplicated Lines Density field, enter a number to define the maximum expected duplicated lines density for the project. The value must be in percentage.
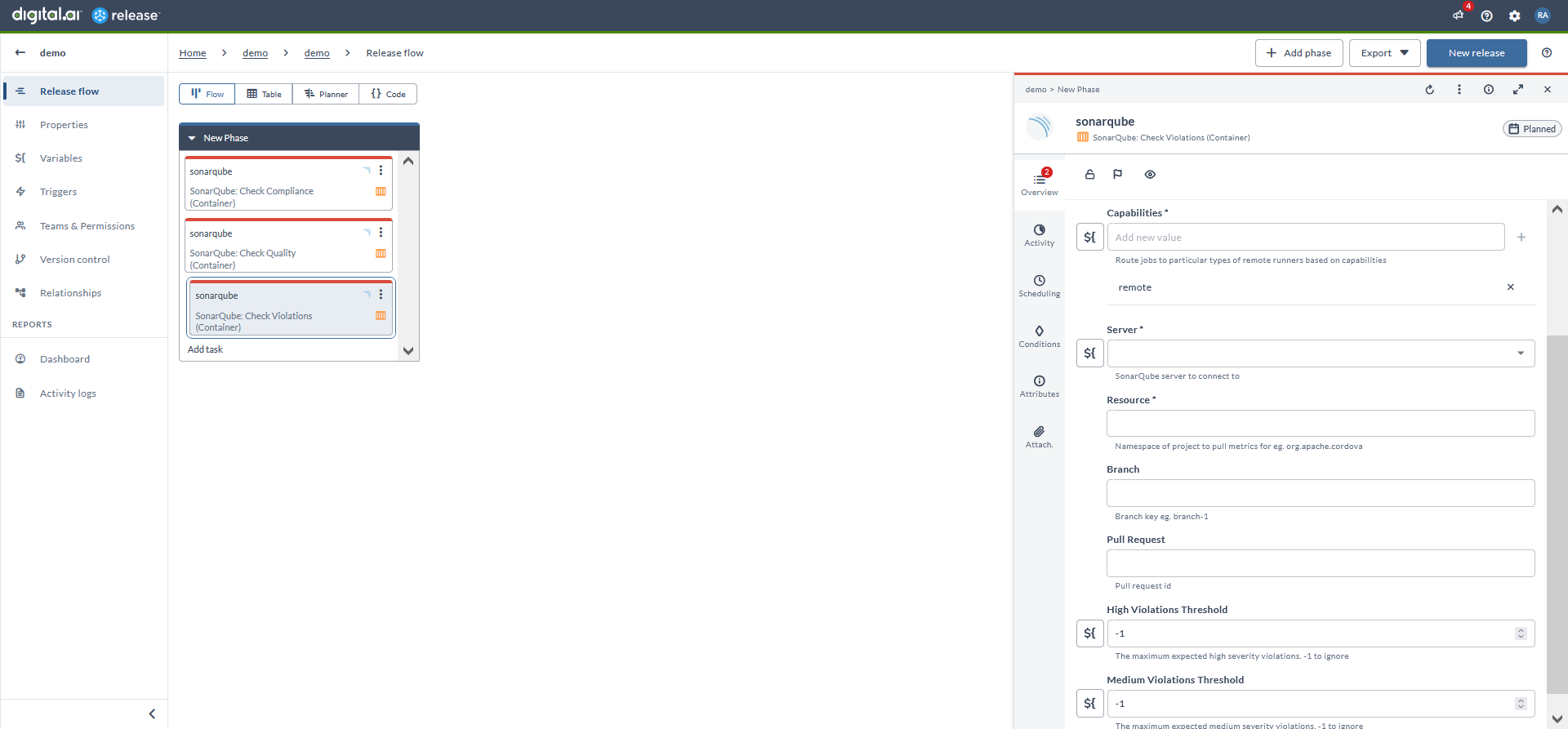
Check Violations (Container)
- In the release flow tab of a Release template, add a task of type SonarQube > Check Violations (Container).
- Click the added task to open it.
- In the Capabilities field, enter a value that matches the capability set for your Runner. This helps you to route jobs to that particular Runner.
- In the Server field, select the configured server.
- In the Resource field, enter the namespace of the project to pull the metrics.
- In the Branch field, enter the name of the GIT branch.
- In the Pull request field, enter the ID of the pull request.
Note: Enter
-1to ignore the following actions.
- In the High Violations Threshold field, enter a number to define the maximum expected high severity violations for the project.
- In the Medium Violations Threshold field, enter a number to define the maximum expected medium severity violations for the project.