Use LDAP for TeamForge User Authentication
LDAP (Lightweight Directory Access Protocol) is an application layer protocol that works on top of the TCP/IP stack and accesses your directory service providers such as Active Directory for providing user authentication. For more information, see RFC2251 - Light-weight Directory Access Protocol (v3).
Enable LDAP as an IdP
This section walks you through the steps to enable LDAP as an IdP in TeamForge.
- Log on to TeamForge as a Site Administrator.
- Select My Workspace > Admin.
- Select Projects > Identity.
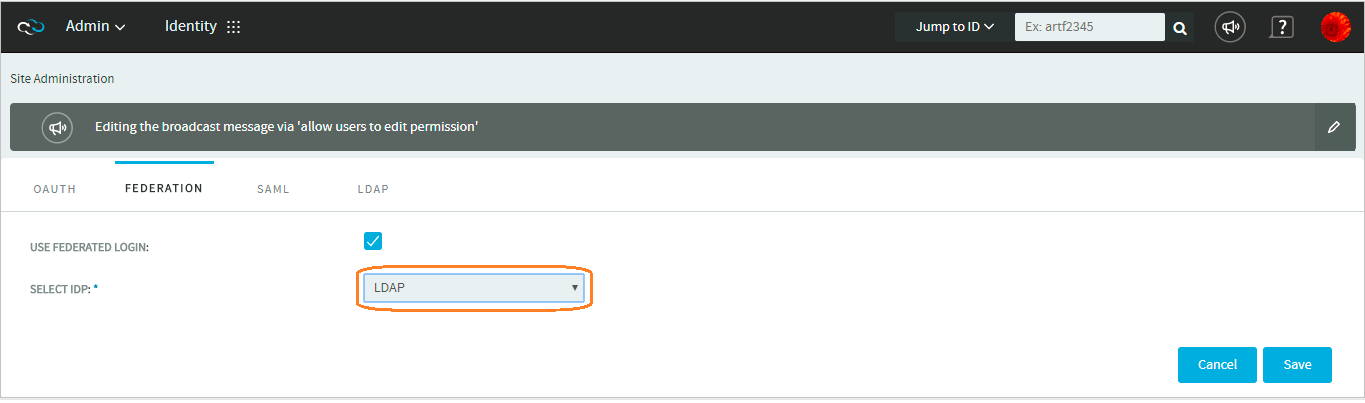
- Select the Federation tab.
- Select the Use Federated Login check box and select LDAP as the IdP from the drop-down list.
- Click Save.
TeamForge-LDAP Authentication--Single LDAP Server Setup
In this section, you can see the configuration required for setting up TeamForge for authentication using a single LDAP server.
-
Once you have your LDAP server set up, you must configure the following
site-options.conftokens in TeamForge before integrating TeamForge with an LDAP server. Use your discretion and configure these tokens to suit your site's requirements. -
In addition to the above tokens, configure the ALLOW DATABASE AUTHENTICATION IF LDAP IS ENABLED parameter. To select this check box, select My Workspace > Admin and select Projects > System Tools > Configure Application. This parameter is listed in the External Authentication section. Select the ALLOW DATABASE AUTHENTICATION IF LDAP IS ENABLED check box to have LDAP credentials stored in TeamForge and have users authenticated via TeamForge every time a user logs in. This helps improve performance by optimizing the number of authentication calls between the TeamForge and LDAP servers.
-
If you have enabled database authentication, LDAP user credentials are stored when users login for the first time and continue to login using the locally stored LDAP credentials. However, you can restrict such indefinite usage of the stored LDAP credentials and force user re-authentication at regular intervals by setting up this configuration parameter. For example, setting a value of
24would force user re-authentication (by the LDAP server) every 24 hours. For more information, see FORCE RE-AUTHENTICATION WITH LDAP SERVER.
-
Log on to TeamForge as a Site Administrator.
-
Select My Workspace > Admin.
-
Select Projects > Identity.
-
Select the LDAP tab. This tab lets you configure the TeamForge-LDAP integration.
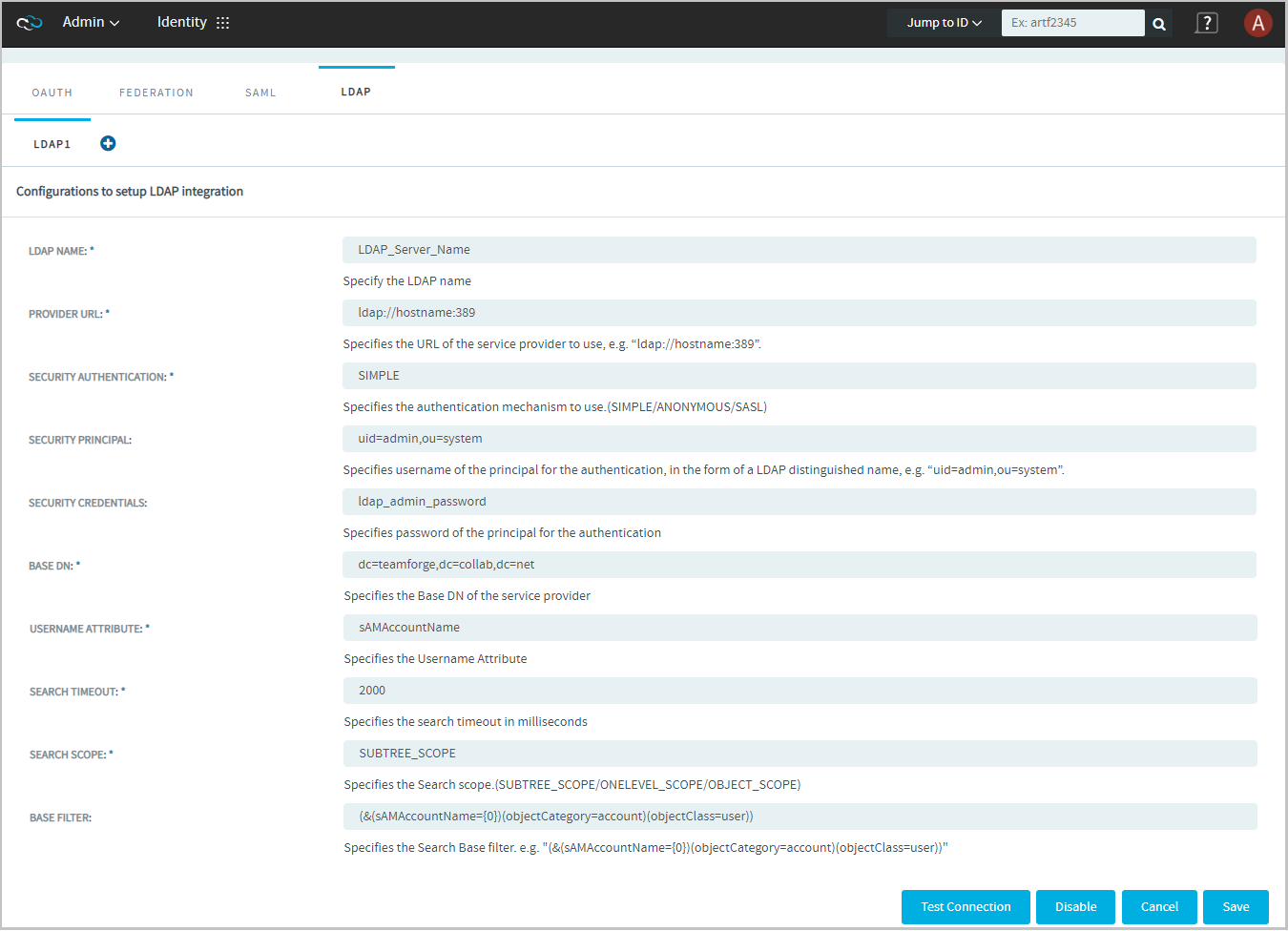
| Fields | Description |
|---|---|
| LDAP NAME | Descriptive name for each LDAP configuration set. |
| PROVIDER URL | The string that encapsulates the IP address and port of a directory server. |
| SECURITY AUTHENTICATION | The authentication method used to bind to the LDAP server. There are 3 types of security authentication in LDAP:
|
| SECURITY PRINCIPAL | The distinguished name of the user to authenticate. Example: "uid=admin,ou=accounts" |
| SECURITY CREDENTIALS | The password or other security credentials of the user to authenticate. |
Note: Select the | |
| BASE DN | The base distinguished name from where a server will search for users. This is a sequence of related distinguished names connected by commas and with the format "attribute=value". Example: dc=help,dc=collab,dc=net |
| USERNAME ATTRIBUTE | Attribute name to be used to match the username provided in the UI.
|
| SEARCH TIMEOUT | The read timeout in milliseconds for an LDAP operation. This is used to control the LDAP request made by a client in a timely manner, so that the client need not wait for a long time for the server to respond. For example, if the search timeout value is 5000 milliseconds, the LDAP service provider can abort the read timeout if the server does not respond within this 5 seconds. |
| SEARCH SCOPE | The starting point of an LDAP search and the depth from the base DN to the levels until which the search should occur. There are three types of search scope in an LDAP search:
|
| BASE FILTER | The group DN in which the users are members, sets the LDAP default search filter for the users to search and load all users from the database of active user accounts belonging to a specific OU (organizational unit) provided in the search filter. This is an optional field. Example value: (&(sAMAccountName=0)(objectCategory=account)(objectClass=user)) |
- Click Save.
If you have issues with a specific LDAP setup, you can disable the LDAP authentication (Click Disable) to troubleshoot and fix the issues.
TeamForge-LDAP Authentication--Multiple LDAP Servers Setup
You can configure multiple LDAP servers for authentication with TeamForge 18.1 and later.
-
Log on to TeamForge as a Site Administrator.
-
Select My Workspace > Admin.
-
Select Projects > System Tools > Configure Application.
-
Set the number of LDAP servers in the LDAP CONFIGURATIONS MAXIMUM LIMIT parameter (in External Authentication section).
-
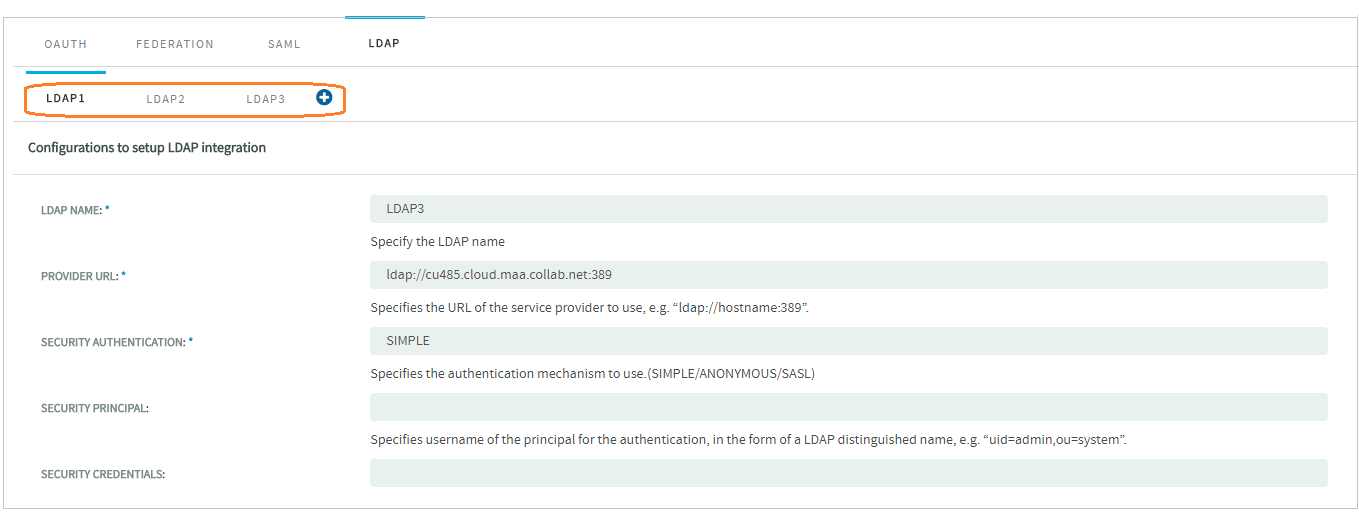
Select Projects > Identity.
-
Select the LDAP tab.
-
Add as many LDAP servers as required (click the
icon) and configure individual LDAP servers as discussed in Set up TeamForge for Single LDAP Server Authentication.
-
Click Save.