CT Security Dataset 1
The CT security dataset enables row-level security by filtering dashboard data based on the logged-in user. It ensures that you see only the data you're authorized to access. This dataset maps your identifiers to relevant project data and is especially useful for dashboards that display sensitive or restricted information.
This dataset excludes records for deleted projects, ensuring that only active project information is included.
CT security datasets 2, 3, 4, and 5 are additional security datasets with the same definitions that you can use to apply data security.
Dataset Components
The following table describes the key attributes of the CT Security dataset:
| Attribute Name | Description |
|---|---|
| Security flag | Indicates whether row-level security is applied. Default value: 'Y'. |
| Security hash | Identifies the project you have access to. |
| Sys_source | Unique identifier of the source. |
This dataset does not include any metrics.
Implementing Row-Level Security
This section explains the use of CT security datasets for implementing row-level data security in dashboards, providing steps and examples for common use cases.
The following datasets are enabled for row-based data security:
- CT security dataset 1
- CT security dataset 2
- CT security dataset 3
- CT security dataset 4
- CT security dataset 5
All other datasets in Continuous Testing are cached by default and are not enabled for row-level security.
These datasets are used to implement security in your dashboard. If your dashboard includes three such as reservation, session, and performance transaction, you may need to use three corresponding security datasets, one for each asset type.
Steps to Enable Row-Level Security in a Dashboard
To enable row-level security in a dashboard using the CT Security dataset:
- Add a Security Dataset: Include the CT security dataset in your dashboard based on the datasets you want to secure.
- Blend Datasets: Join the security dataset with the target dataset using the appropriate security hash and project attributes.
- Apply the Security Flag: Add the
Security flagattribute from the security dataset as a global filter. Set the filter value to 'Y'.
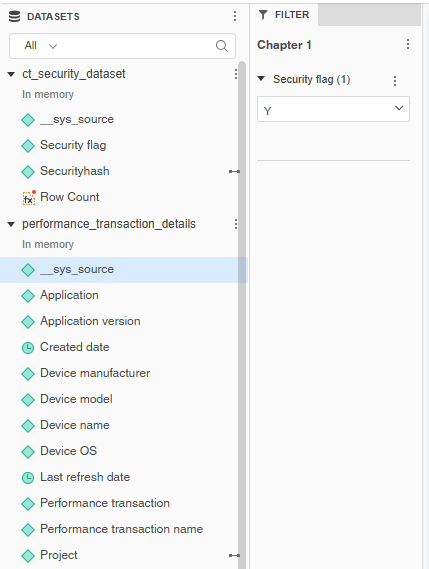
Use Case 1: Securing with CT Security Dataset
You can use the CT security dataset when you want to apply security to a dataset that is not secured by default.
Datasets Used:
- CT security dataset 1 (secured)
- Performance transaction details (not secured)
Steps:
- Right-click the
Security hash 1attribute, select Link to Other Dataset, and then select theProjectattribute from the Performance transaction details dataset. - On the View menu, select Filter Panel.
- Select the ellipsis (…), point to Add Filters, select
Security flag 1, and then click OK.
Use Case 2: Securing Multiple Independent Datasets
You can use this method when your dashboard includes multiple datasets that require individual security configurations.
Datasets Used:
- CT security dataset 1 (secured)
- CT security dataset 2 (secured)
- Performance transaction details (not secured)
- Reservation base (not secured)
Steps:
- Right-click the
Security hash 1attribute, select Link to Other Dataset, and then select theProjectattribute from the Performance transaction details dataset. - On the View menu, select Filter Panel.
- Select the ellipsis (…), point to Add Filters, select
Security flag 1, and then click OK. - Right-click the
Security hash 2attribute, select Link to Other Dataset, and then select theReservation projectattribute from the Reservation base dataset. - On the View menu, select Filter Panel.
- Select the ellipsis (…), point to Add Filters, select
Security flag 2, and then click OK.
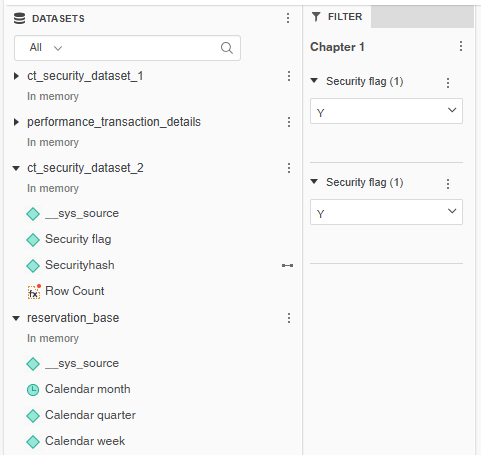
The dashboard will enforce row-level access controls for both datasets independently.