Hashicorp Vault Plugin
This topic covers the HashiCorp Vault Plugin for Release, which integrates Vault for secure secret management within release pipelines.
The HashiCorp Vault plugin retrieves secrets from a Vault Server for use in your tasks and automation. These secrets include static and dynamic username and password fields from the Secrets Engine of your choice.
Requirements
- Digital.ai Release: version 9.6+
Installation
This documentation assumes gradle version 6.0.1. See gradle/wrappter/gradle-wrapper.properties for the actual version.
Import the jar file into your %XLRELEASE_INSTALLATION%/plugins/xlr-official folder,
or from the Digital.ai Release web UI as a new plugin. Adding the plugin requires a server restart.
Authentication
Vault permits several types of authentication as outlined in the Hashicorp Vault Authentication documentation.
Note: This plugin implements a subset of the authentication options, namely token. Other authentication options can be added as demanded. With 23.1 a new type of authentication called Basic is introduced for the HashiCorp Vault plugin.
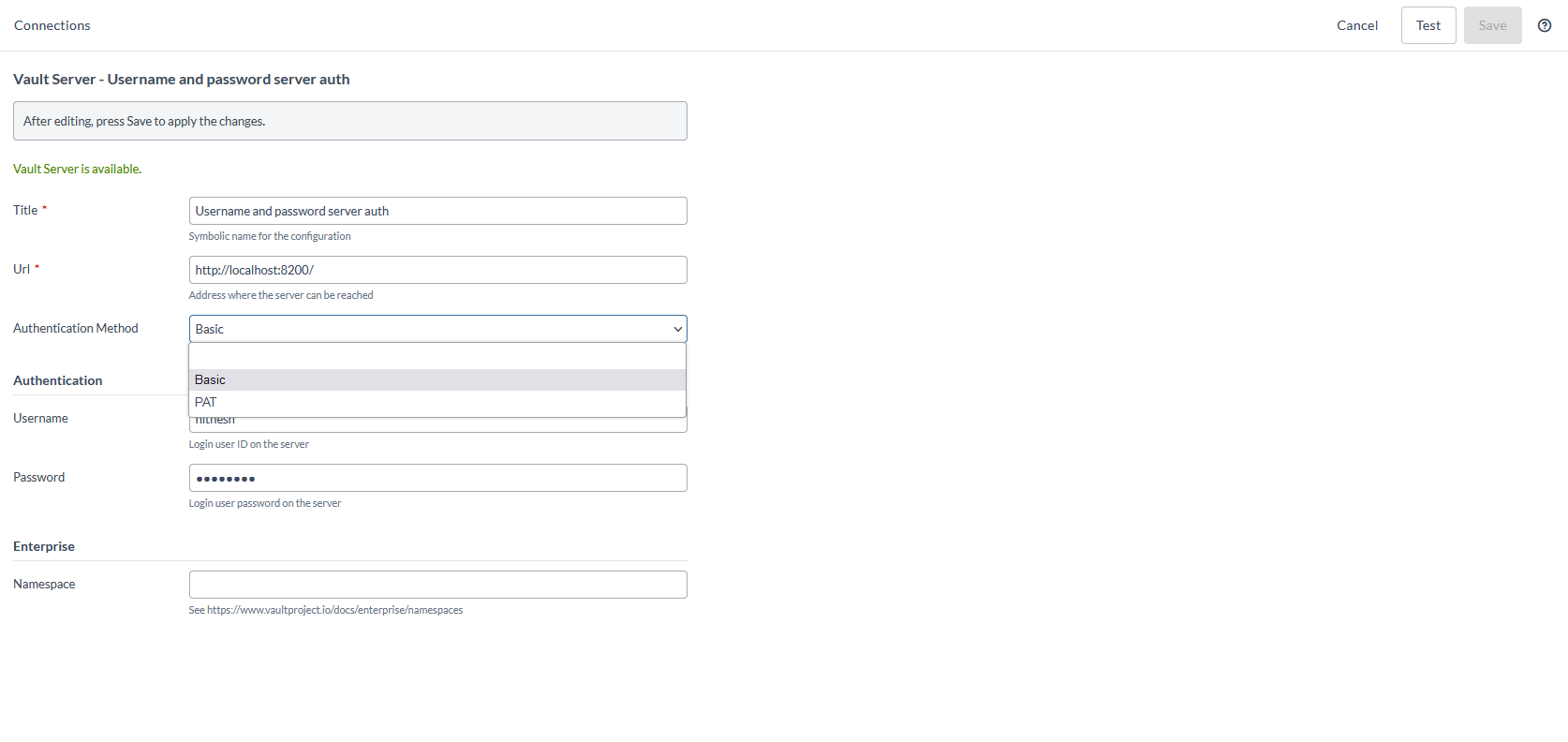
Define the server configuration of URL, select from the dropdown menu Authentication Method.
The Hashicorp Vault plugin now includes support for LDAP authentication method.
Along with Token authentication, Basic authentication is now introduced for HashiCorp Vault plugin.
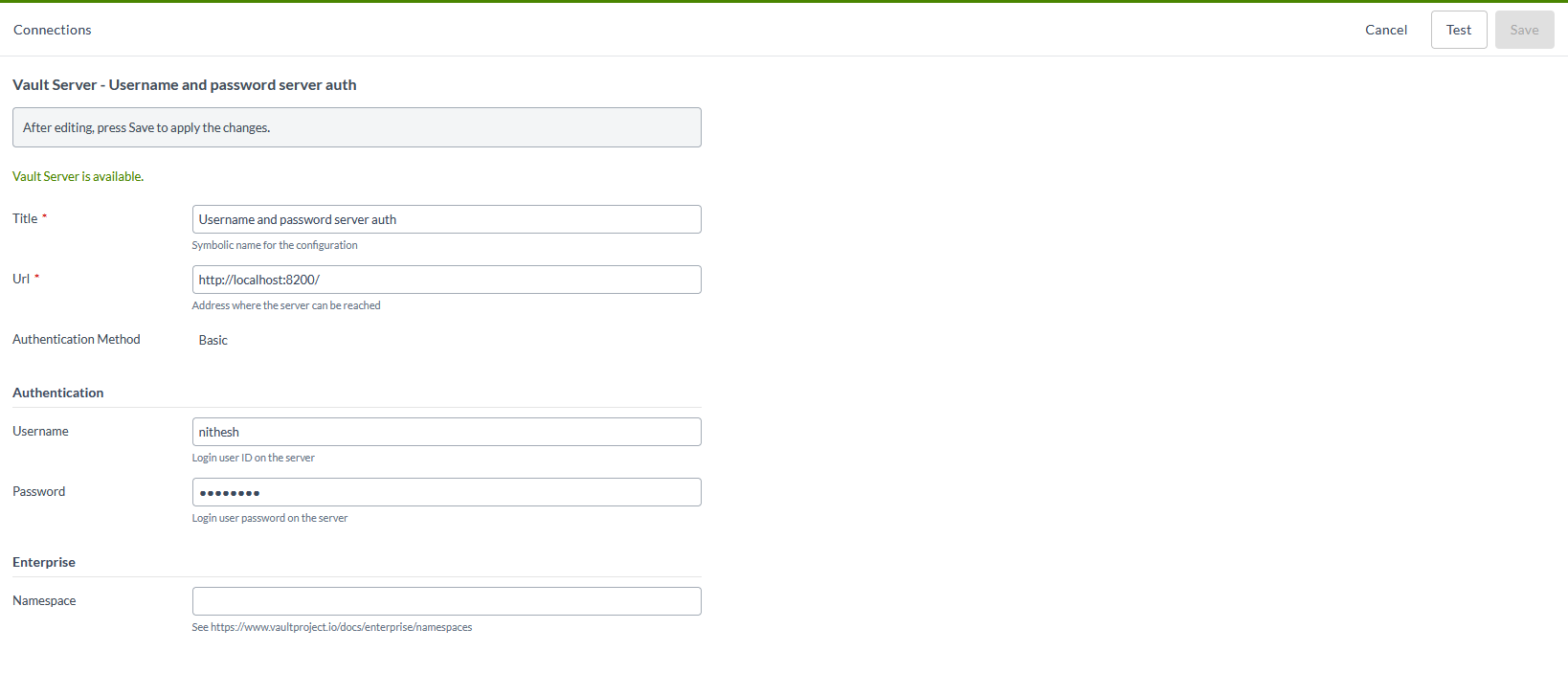
Various types of authentication are added to the HashiCorp Vault plugin.
- If PAT is selected, The URL and Token are added as authentication fields in the HashiCorp Vault plugin.
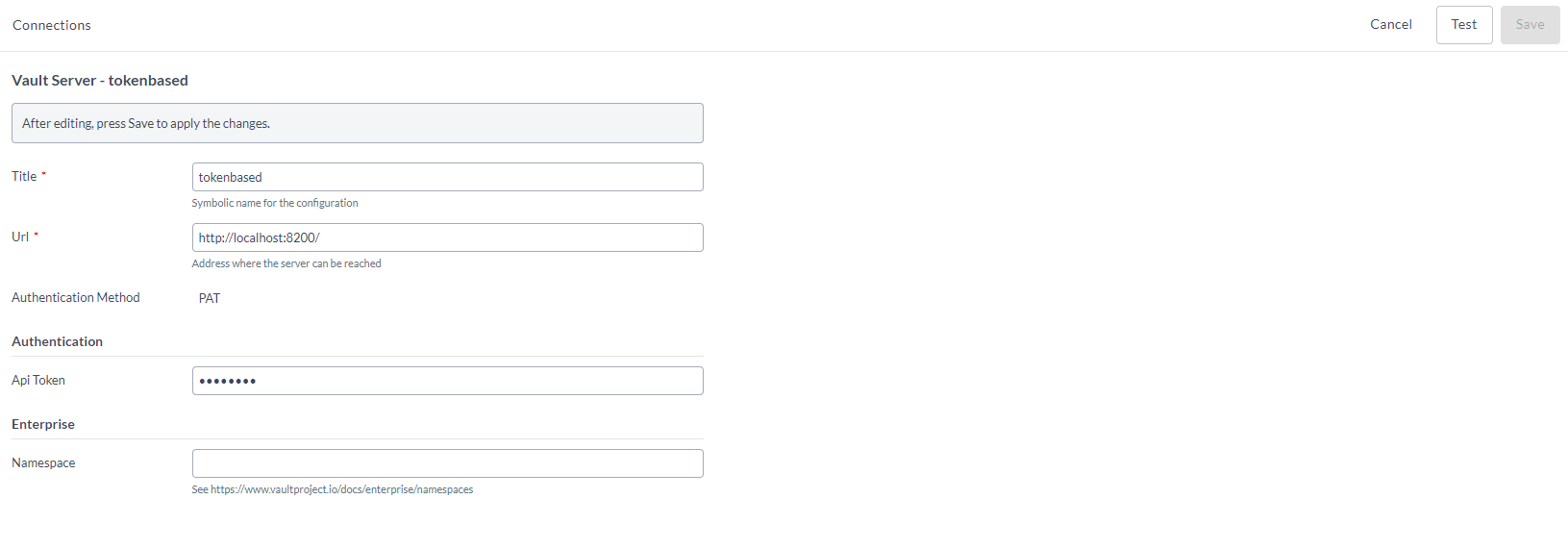
Define the server configuration of URL plus token or Basic
- If Basic is selected, The URL, Username and Password are added as authentication fields in the HashiCorp Vault plugin.

Read Secret task for KV Version2 mount type is added to the HashiCorp Vault plugin.
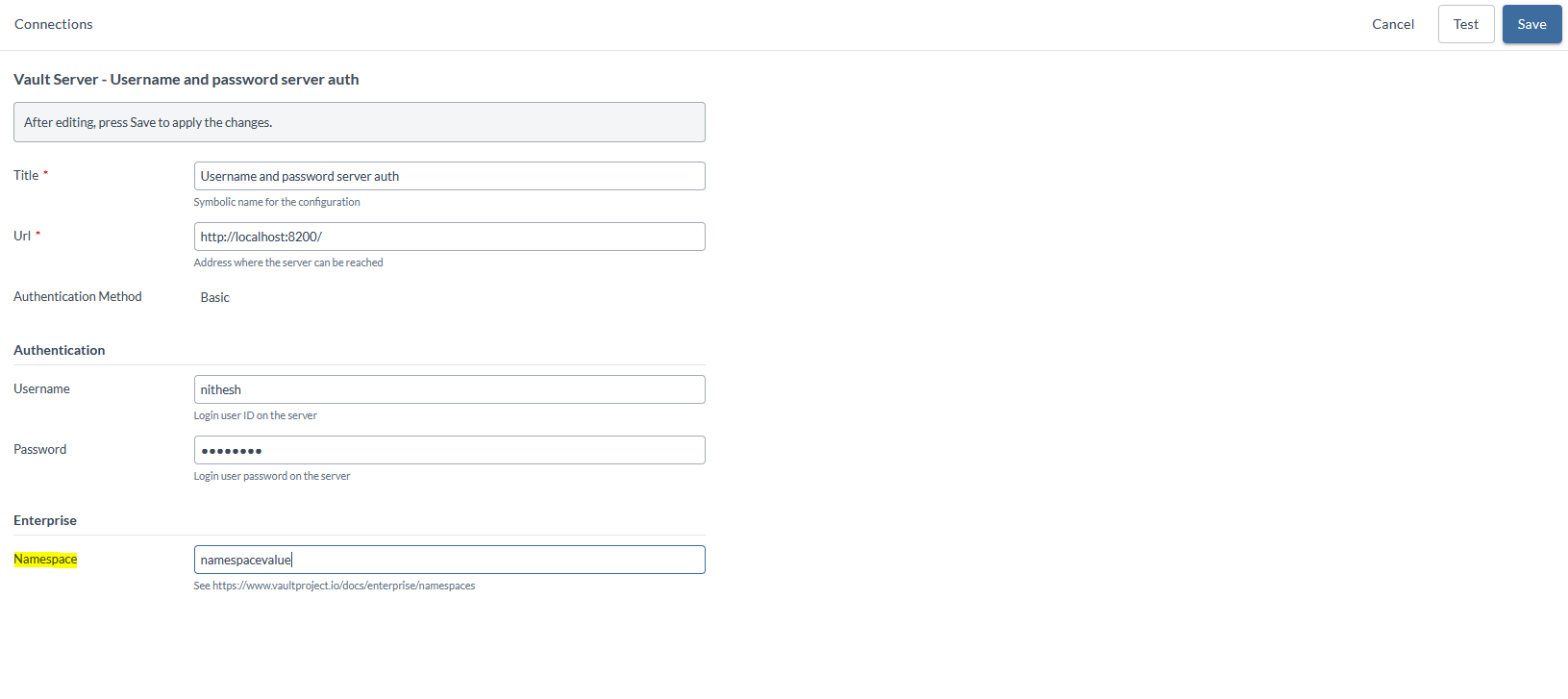
Namespace field is added to the HashiCorp Vault plugin.
Note: Vault should run in Enterprise mode to have a namespace.
List Of Various Tasks in Vault plugin.
KV version1 Tasks
- SecretsV1-ReadDynamicSecret
- SecretsV1-CreateSecret
- SecretsV1-ReadSecret
- SecretsV1-DeleteSecret
- SecretsV1-EnableEngine
KV version2 Tasks
- SecretsV2-ReadSecret
- SecretsV2-EnableEngine
- SecretsV2-Configure
- SecretsV2-ReadConfiguration
- SecretsV2-ReadSecretVersions
- SecretsV2-CreateSecret
- SecretsV2-PatchExistingSecret
- SecretsV2-DeleteVersion
- SecretsV2-UndeleteVersion
- SecretsV2-DestroyVersion
- SecretsV2-ListSecrets
- SecretsV2-ReadSecretMetadata
- SecretsV2-UpdateMetadata
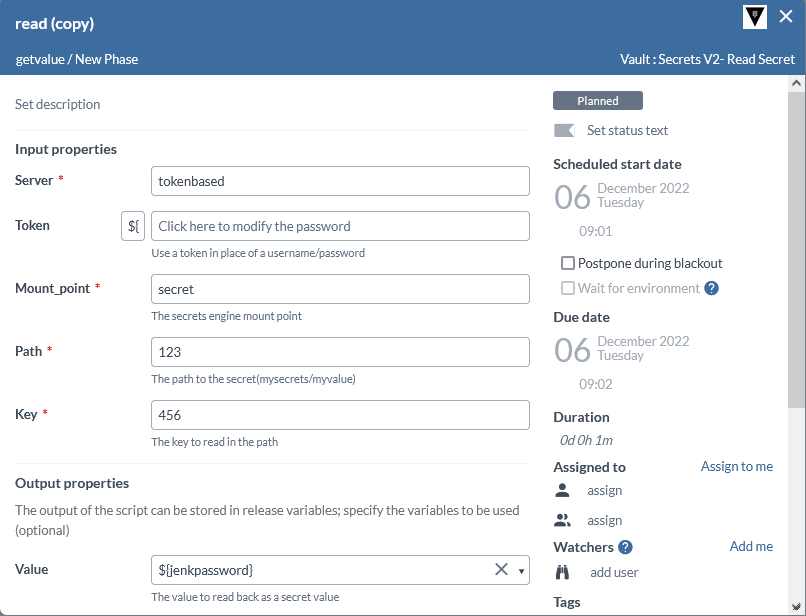
Read Secret KV version2
Read Secret task for KV Version2 need to specify the Mount_point, Path and Key. Based on the path and key we will get the data which can be stored as a output variable.

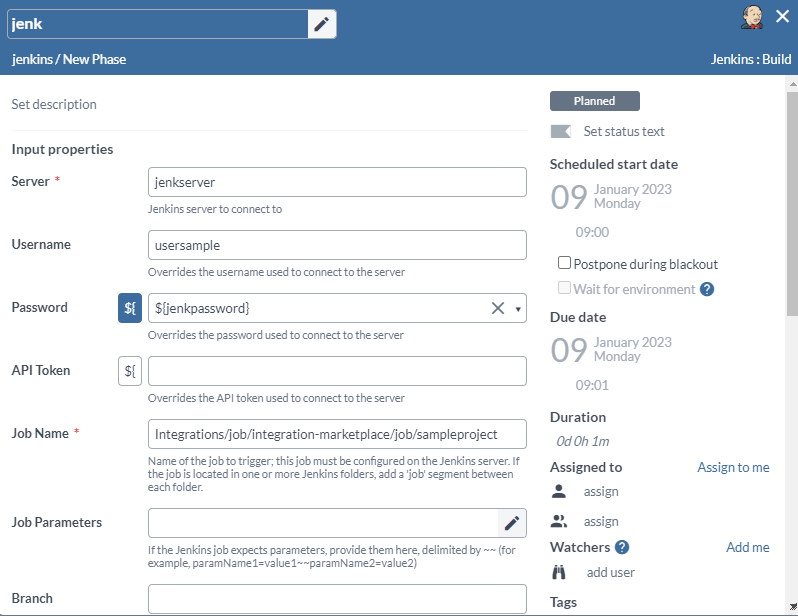
Use the Secret as Part of Another Task
In this example, the Hashicrop Vault Get Secret V2 task is followed by a Jenkins Build Task. The Jenkins task makes use of the release variable 'jenkpassword' (previously populated by Vault) as the Jenkins password (overriding the password configured for the Jenkins server).