Manage secrets using Azure Keyvault
Your development organization may choose to integrate with an external secrets management tool to support the secure management of secrets. While you can choose to manage sensitive key/value pairs for environment-specific information using internal encrypted dictionaries. Deploy also supports integration with the Azure keyvault service to manage and inject secrets into Deploy. The API-based integration with Azure keyvault enables you to define, manage, and use keyvault as an external data source for secret storage.
How it works
The Azure keyvault integration is a Deploy plugin that allows you to configure external dictionaries that can be used with your environments. You can also define a Azure keyvault-based lookup provider that can reference and resolve a key/value pair stored in keyvault secrets. Deploy does not save or cache the key/value information stored in Azure keyvault in the Deploy system.
Use external Azure keyvault-based dictionaries
Managing an external Azure keyvault dictionary is similar to how you currently manage internal dictionaries in Deploy.
- You assign a Vault-based dictionary to an environment.
- During deployment, key/value pairs stored in Vault will replace defined placeholders in the deployment to the environment.
To manage a Vault dictionary, you:
- Define a connection to your Vault server and the paths to where secrets and values are stored.
- Define an external dictionary using this connection.
- Associate the external dictionary with an environment.
- Create placeholder references to secrets and other values stored in Azure keyvault.
Use an external Azure keyvault lookup provider
For secrets and password fields used with certain CI's, you can establish a Azure keyvault-based lookup provider that will be used to look up a value based on a lookup provider key that you specify. See Create an external lookup value provider for details.
User access control
Like any security-related feature, controlling access to sensitive data needs to be managed as a part of the integration. Deploy provides controls to limit access, ensuring that:
- Developers are authenticated and authorized to read secrets
- Role-based access to secrets is supported
- Policies are provided to control credentials and how they can be used
The integration with Vault is controlled by the connection to the Azure Keyvault server itself and the specific list of keys (Secret paths) that the user can access.
Install the plugin
To install the plugin:
- Download the Deploy Azure Keyvault integration from the distribution site.
- Place the plugin inside the
XL_DEPLOY_SERVER_HOME/plugins/directory. - Restart Deploy.
For additional details on installing or removing a plugin, see Install or remove Deploy plugins.
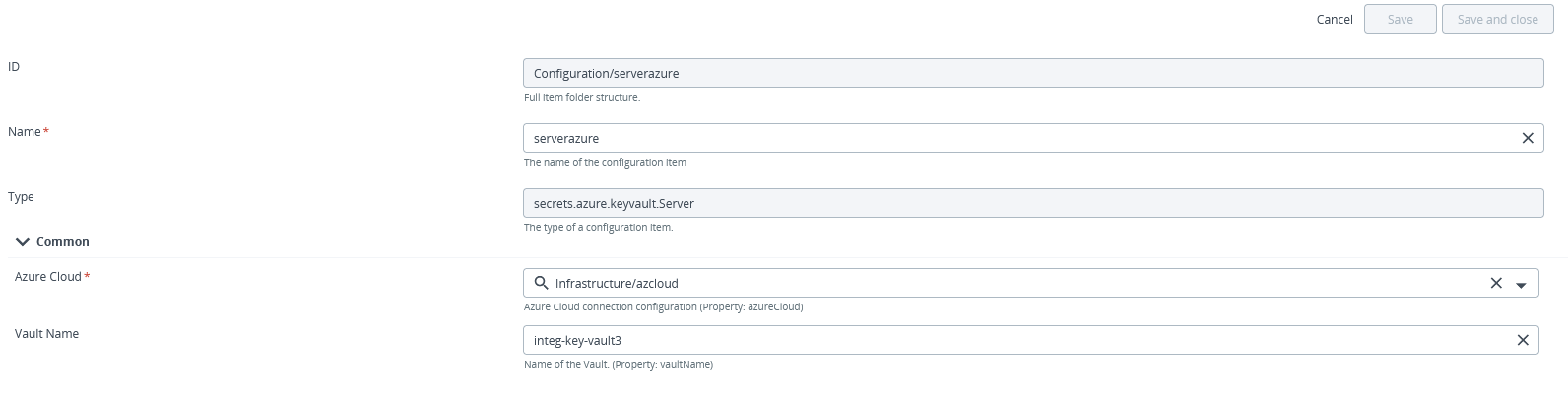
Create a HashiCorp Vault connection
Deploy supports the Azure keyvault using a 'Server' CI configuration type. The role of this type is to allow you to configure a connection to a Azure keyvault server using the Azure Cloud connection and be able to read key values.
To create a new connection to a Vault server:
-
Hover over Configuration, click
, and select New > secrets > azure > keyvault > Server.
-
In the Name field, enter a name for the Azure keyvault connection.
-
In the Azure Cloud field, select an predefined Azure server for connection.
-
In the Vault Name field, enter a name of the keyvault.
-
Click Save or Save and close.
Create an external lookup value provider
You can specify certain properties for a Configuration Item (CI) that should be looked up in an external source. This is useful for sensitive data that is not part of a deployment package such as hosts or cloud targets.
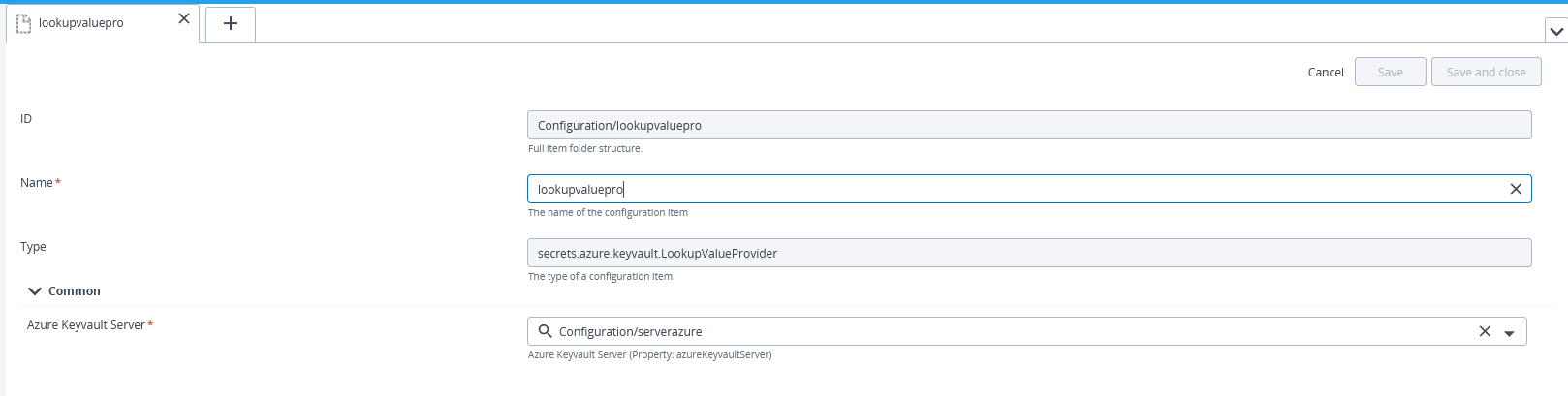
To support this, you can create a special CI type called a LookupValueProvider that references your Vault connection. Once this configuration is in place, you can select the LookupValueProvider and type a key/identifier for the value that you want to use.
To create Vault lookup provider:
-
Hover over Configuration, click
, and select New > secrets > azure > keyvault > LookupValueProvider.
-
In the Name field, enter a name for the Azure Keyvault lookup provider.
-
In the azure-keyvault-lookup-provider field, enter the name of the Azure Keyvault server connection you created earlier (e.g., MyAzureVault).
-
Click Save or Save and close.
Create an external dictionary
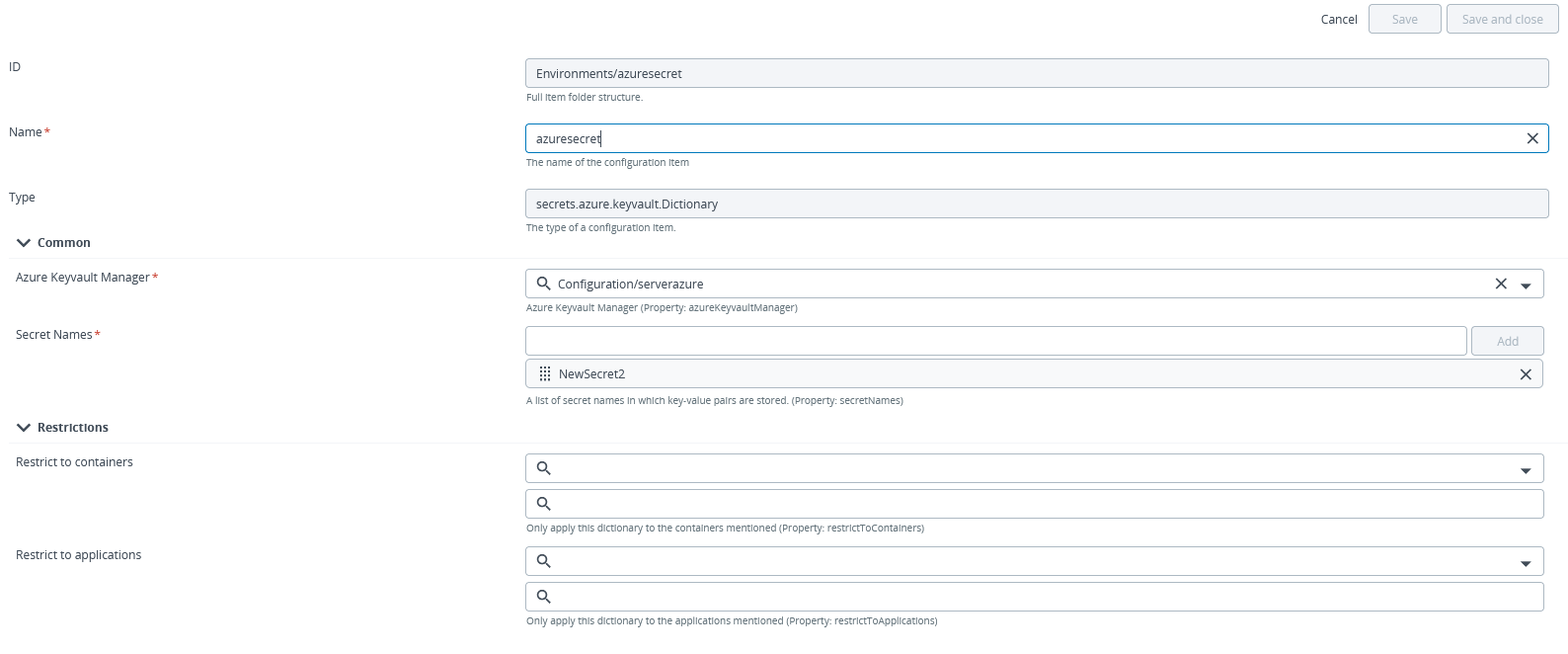
Once you have defined your external Azure keyvault server connection, you can create a dictionary that you can associate with your environments. To create an external dictionary:
-
Hover over Environments, click
, and select New > secrets > azure > keyvault > Dictionary.
-
In the Name field, enter a name for the Vault dictionary.
-
In the Azure Keyvault Manager field, enter the name of the Vault server connection you created earlier (e.g., MyAzureVault).
-
In the Secret paths field, type one or more secret paths to where key-value pairs are stored.
-
Click Save or Save and close.
Select an external lookup value provider and key
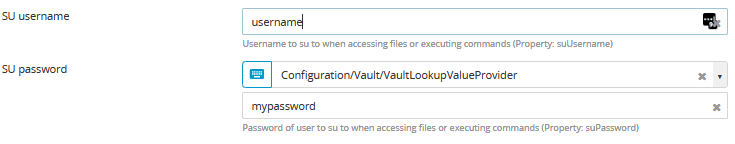
After creating an external lookup value provider, you can now select it and choose a key when configuring properties for certain CIs. For example, if you want to store and resolve a password for a host CI:
-
Hover over Infrastructure, click
, and select New > overthere > SshHost.
-
Complete the required fields for the CI.
-
In the SU password field, click
and select the LookupProvider you created in Create an external lookup value provider.
-
In the Lookup provider key field, type the name of the key for the corresponding value that is stored in Azure keyvault.
-
Click Save or Save and close.