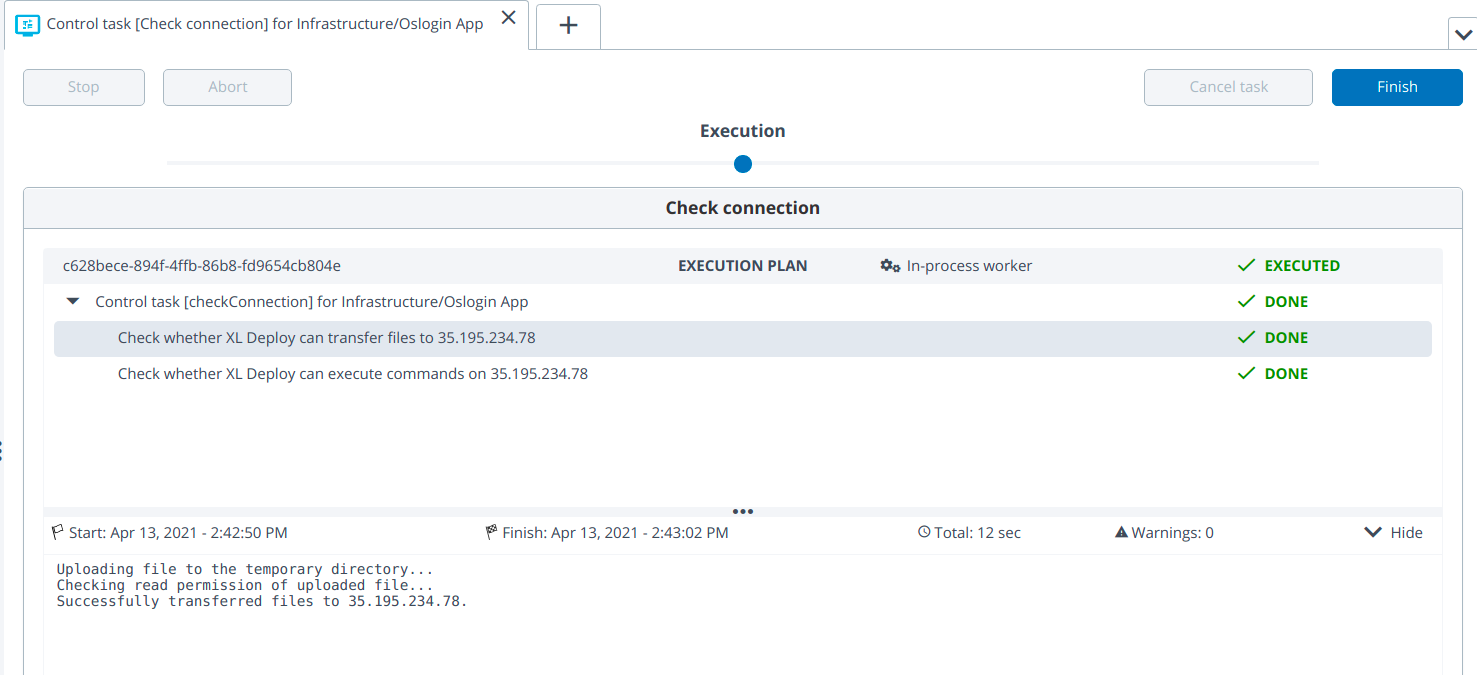
Verify oslogin and metadata ssh connection to GCP instance
This topic provides information on verifying OS login and metadata SSH connections to a GCP instance. It includes steps to ensure that OS login is properly configured and that SSH connections using metadata are functioning correctly.
Pre-requites before verifying oslogin and Metadata SSH connection to GCP instance
- User should have account in GCP (Google Cloud Platform)
- User should have created a project in GCP
- User should have created a service account
- Clone overthere repository.
Verify oslogin and Metadata SSH connection to GCP instance
To verify oslogin and Metadata SSH connection to GCP instance, do the following steps:
-
Run the
export GOOGLE_APPLICATION_CREDENTIALS=/path/to/jsonfileand start the Digital.ai Deploy server. -
Create DefaultGcpCredentials by hover over the Configuration, click
then select New > credentials > gcp > DefaultGcpCredentials under the Configuration.
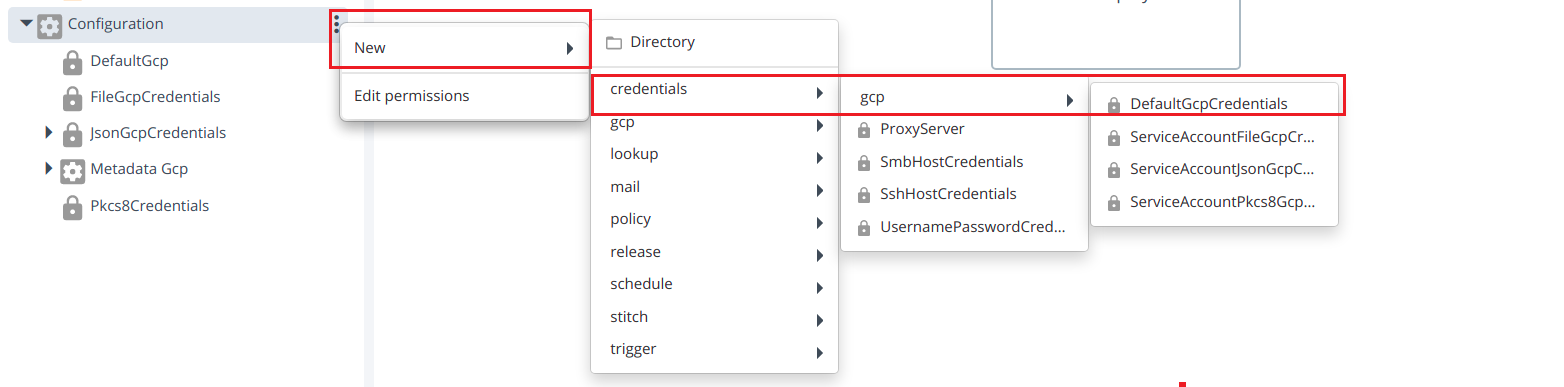
Provide the required inputs to the fields in the DefaultGcpCredentials:
- Username
- Password
- Project ID
- Client email address of the service account
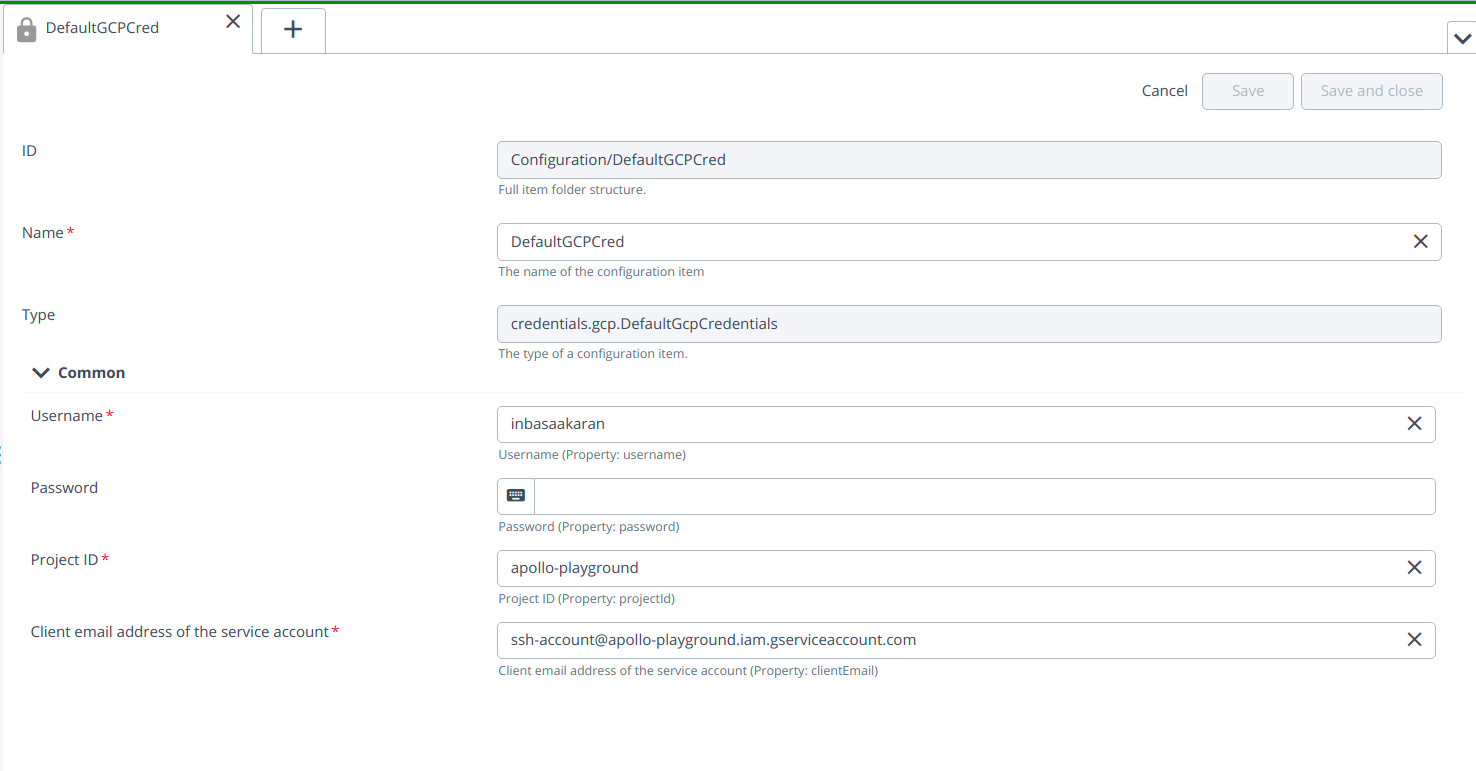
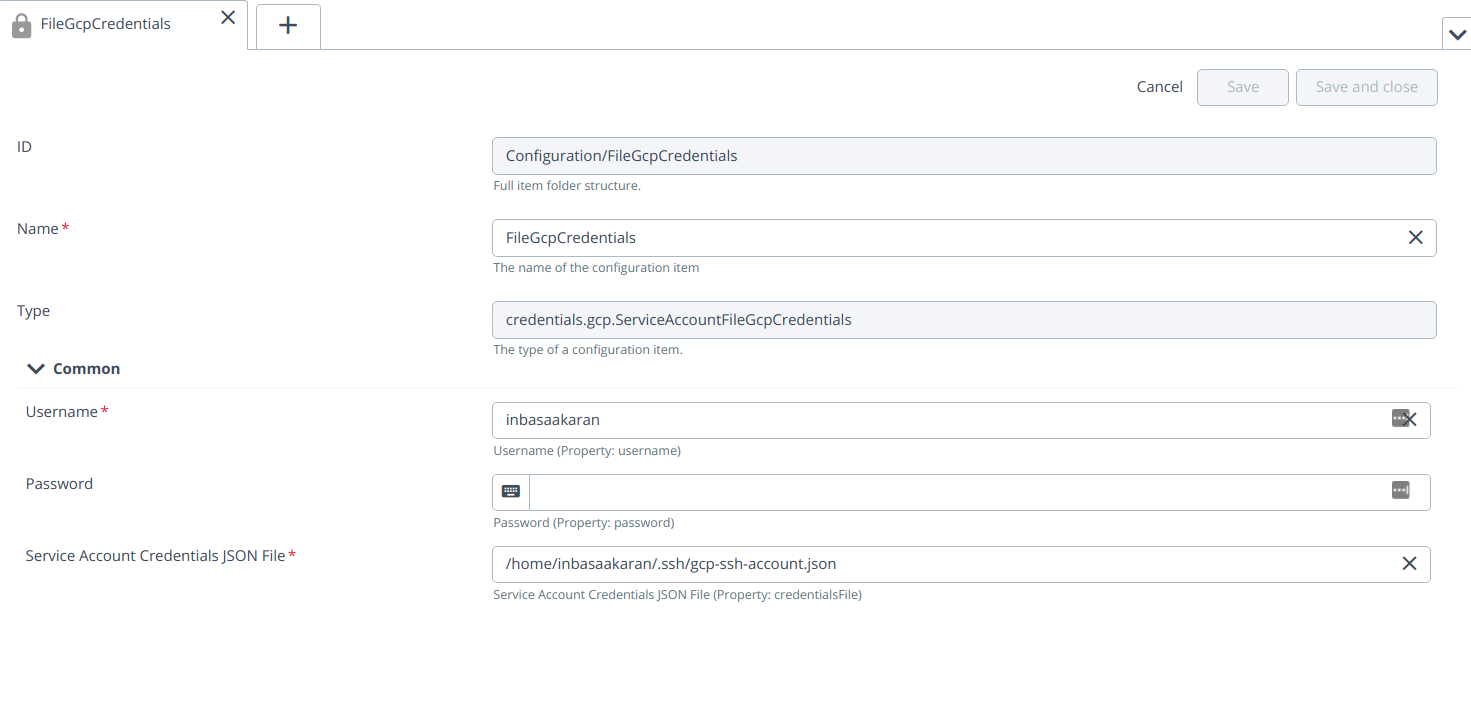
- Create ServiceAccountFileGcpCredentials by hover over the Configuration, click
then select New > credentials > gcp > ServiceAccountFileGcpCredentials under the Configuration.
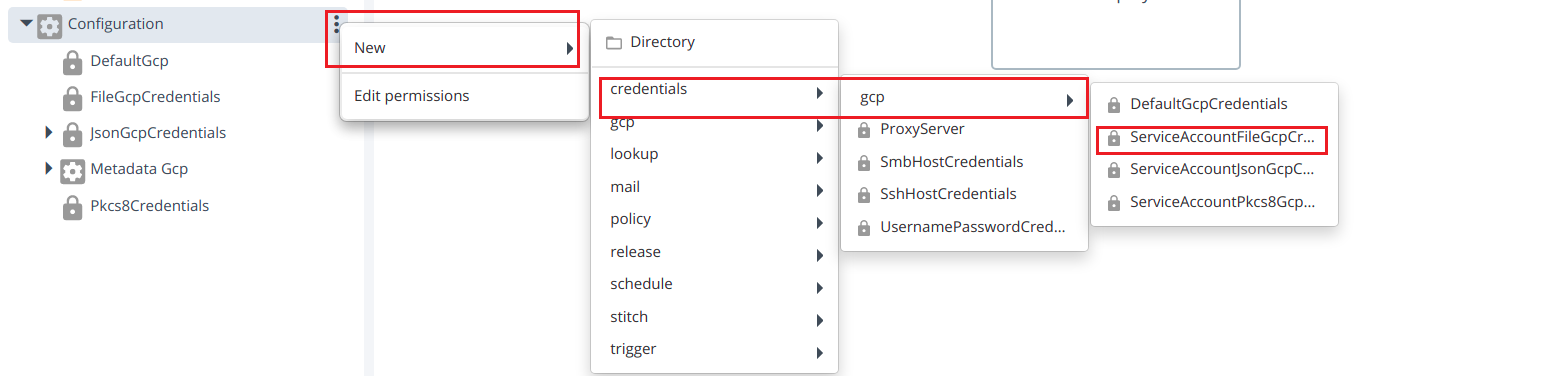
Provide the required inputs to the fields in the ServiceAccountFileGcpCredentials:
- Username
- Password
- Service Account Credentials JSON File
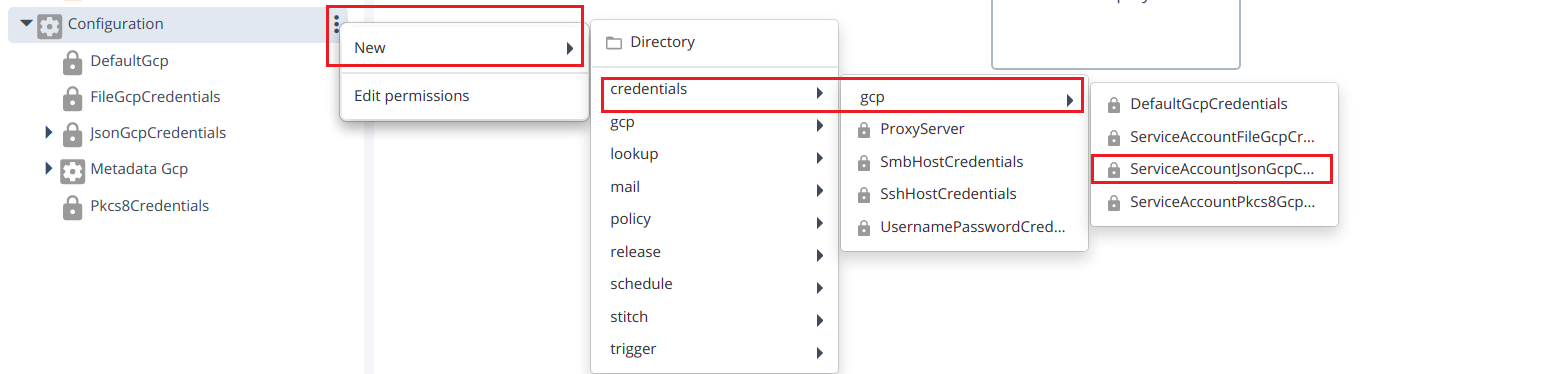
- Create ServiceAccountJsonGcpCredentials by hover over the Configuration, click
then select New > credentials > gcp > ServiceAccountJsonGcpCredentials under the Configuration.
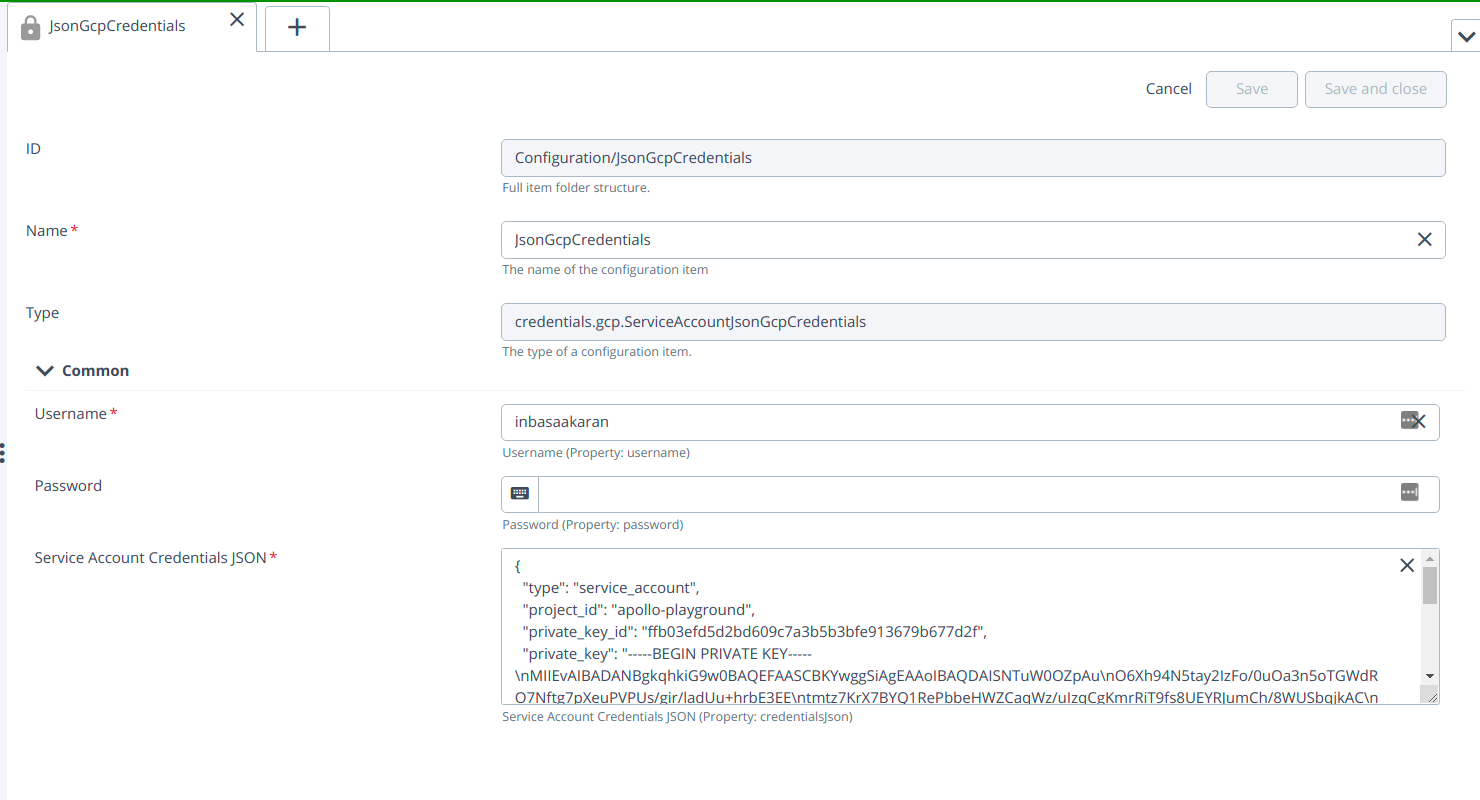
Provide the required inputs to the fields in the ServiceAccountJsonGcpCredentials:
- Username
- Password
- Service Account Credentials JSON File (copy and paste the credentials from JSON file).
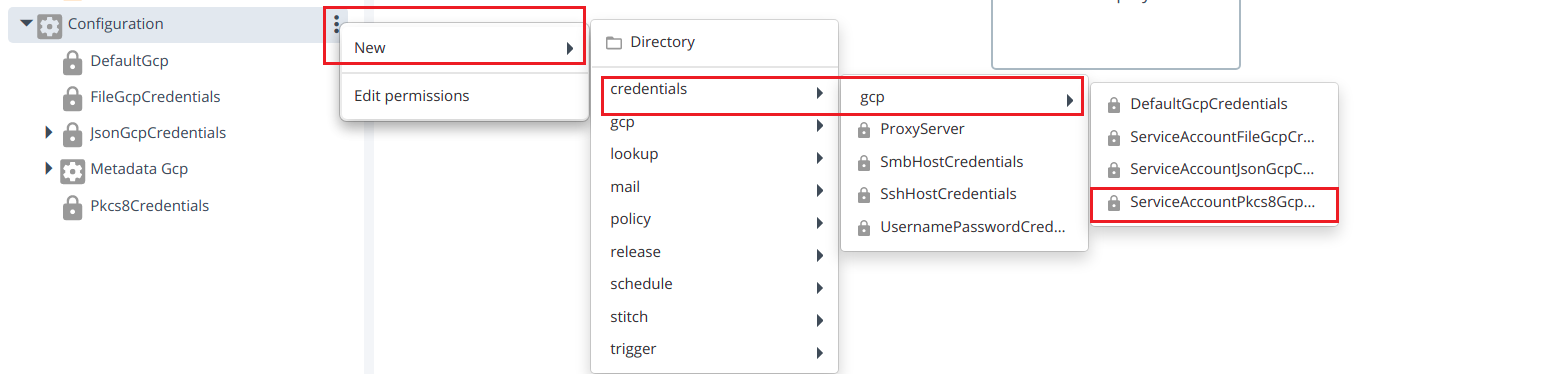
- Create ServiceAccountPkcs8GcpCredentials by hover over the Configuration, click
then select New > credentials > gcp > ServiceAccountPkcs8GcpCredentials under the Configuration.
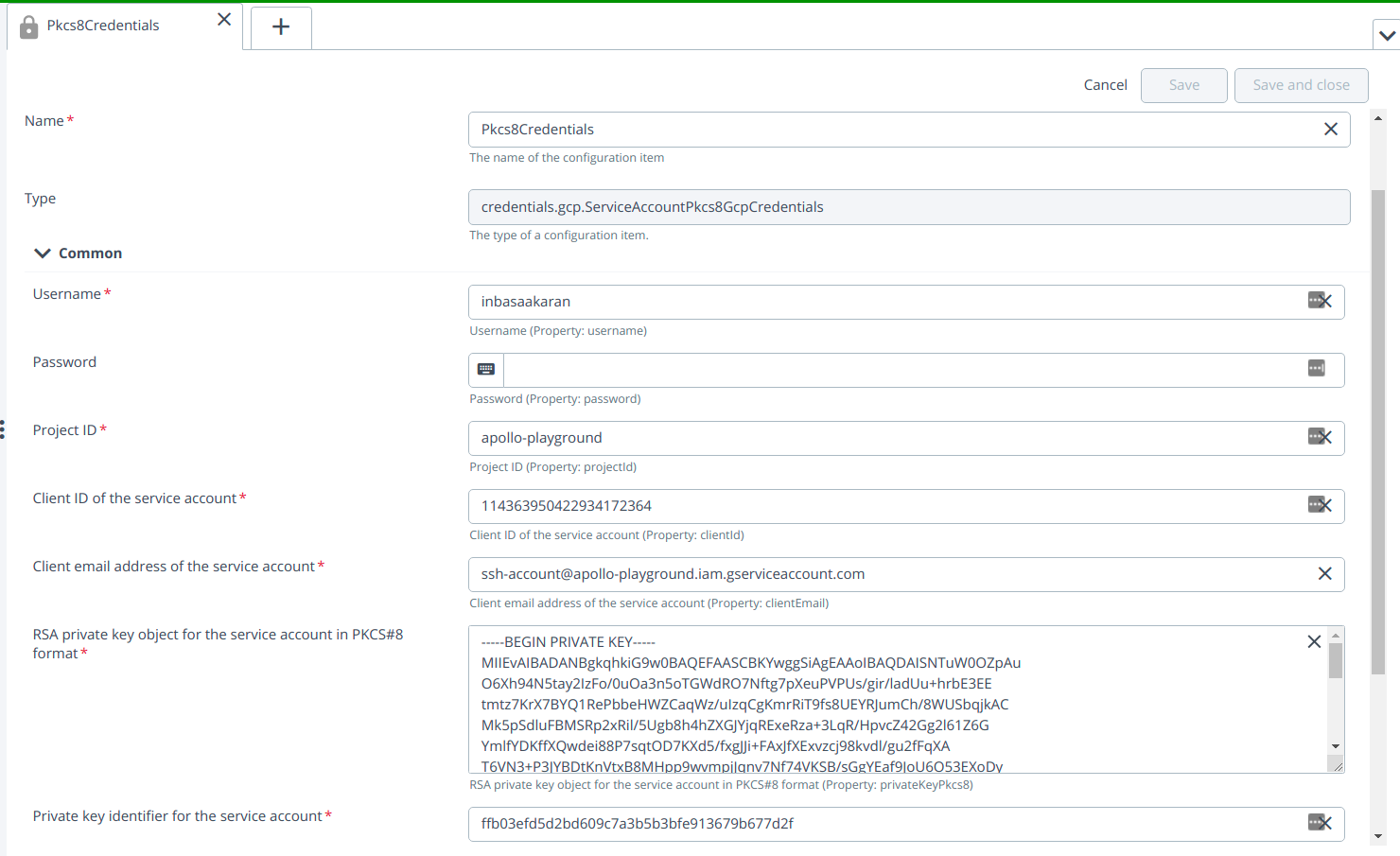
Provide the required inputs to the fields in the ServiceAccountPkcs8GcpCredentials:
- Username
- Password
- Project ID
- Client ID service account
- Client email address of the service account
- RSA private key object for the service account in PKCS#8 format
- Private key identifier for the service account.
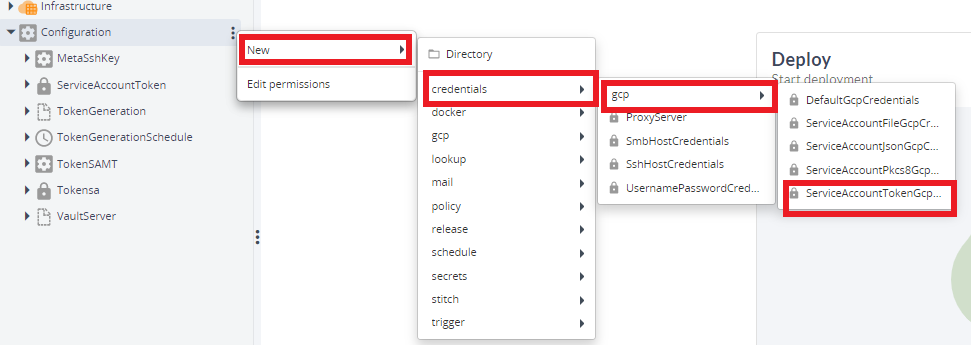
- Create ServiceAccountTokenGcpCredentials by hover over the Configuration, click
then select New > credentials > gcp > ServiceAccountTokenGcpCredentials under the Configuration.
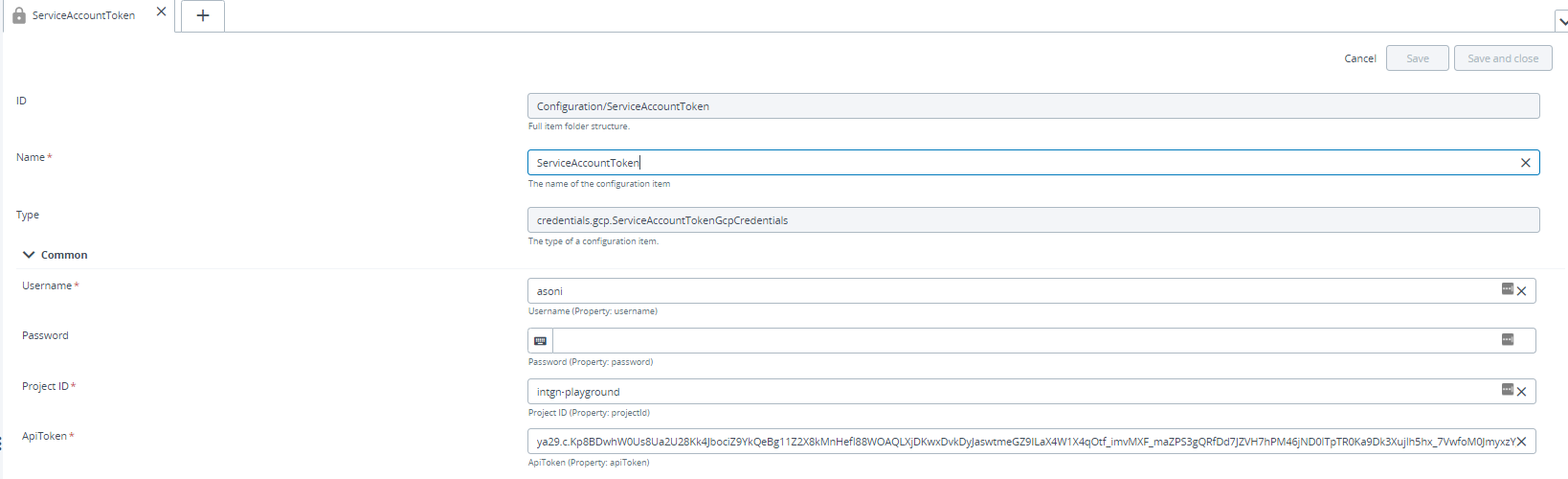
Provide the required inputs to the fields in the ServiceAccountJsonGcpCredentials:
- Username
- Project ID
- ApiToken
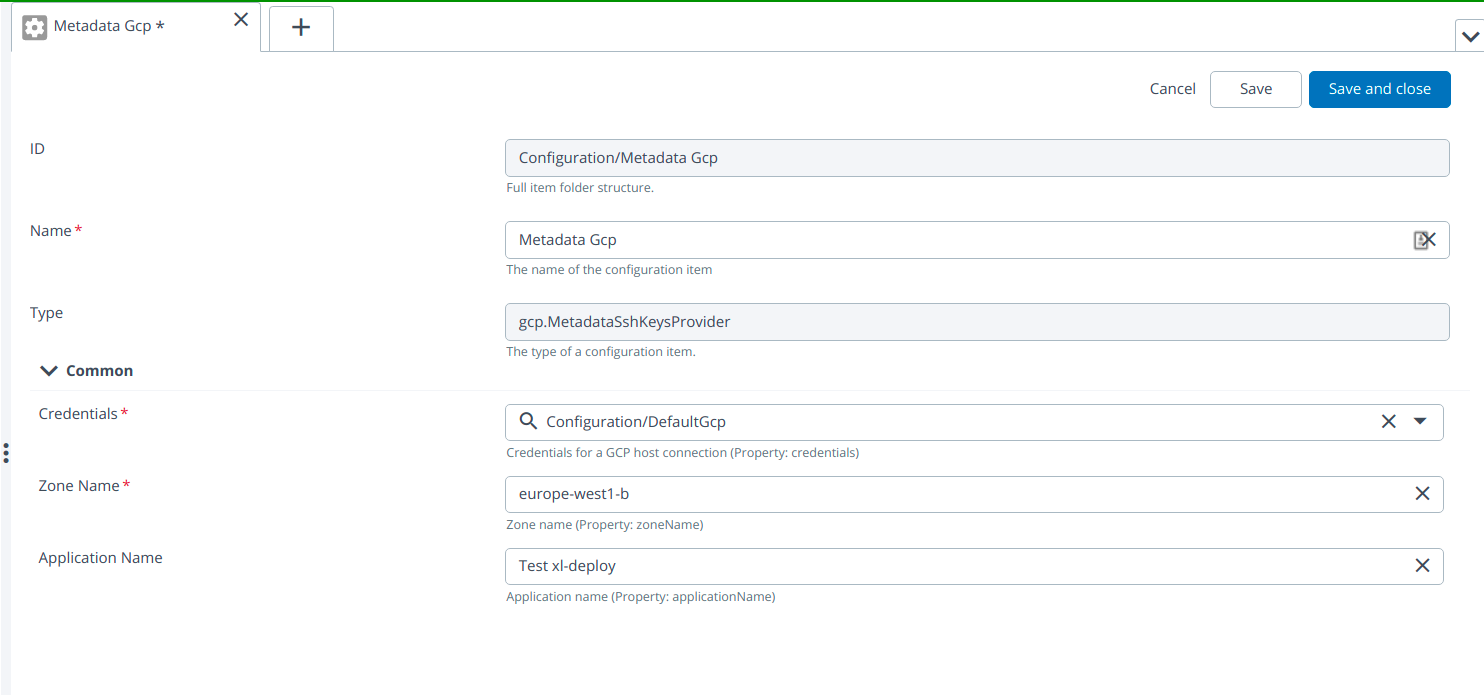
- Create MetadataSshKeysProvider by hover over the Configuration, click
then select New > gcp > MetadataSshKeysProvider under the Configuration.
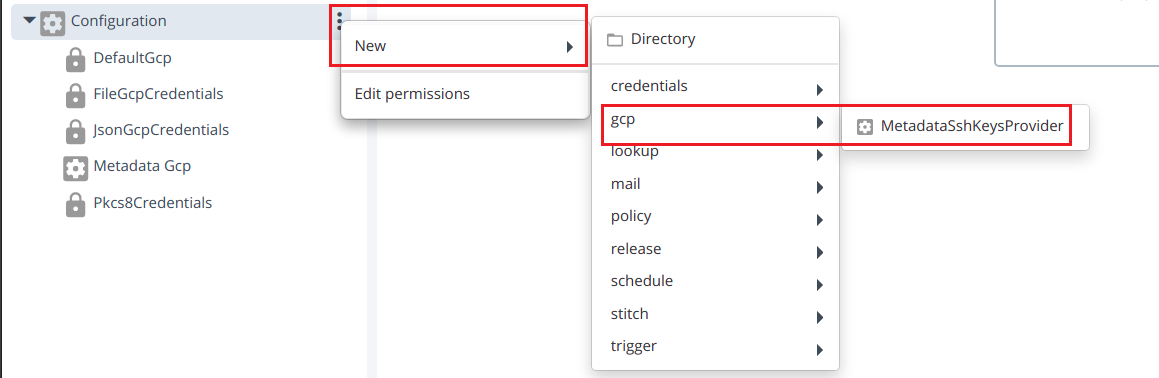
Provide the required inputs to the fields
- Credentials
- Zone Name.
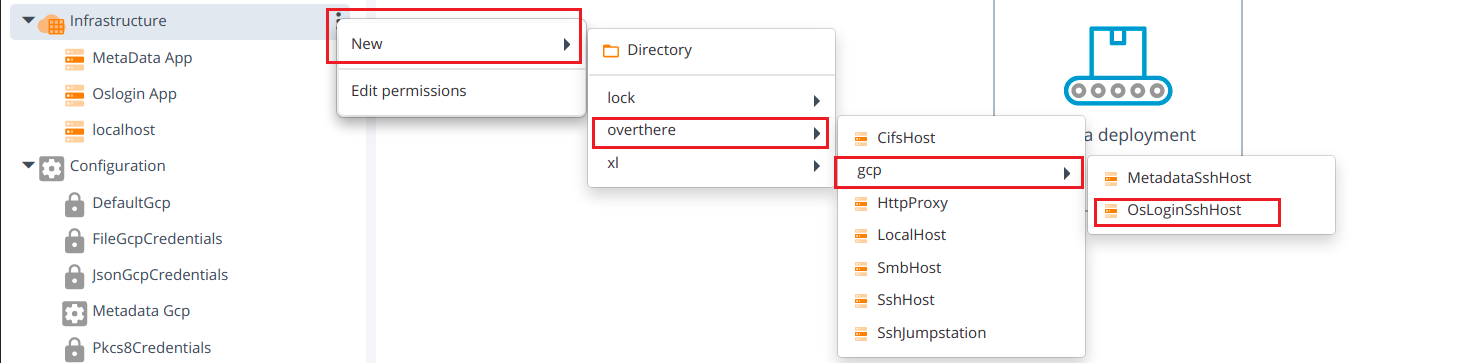
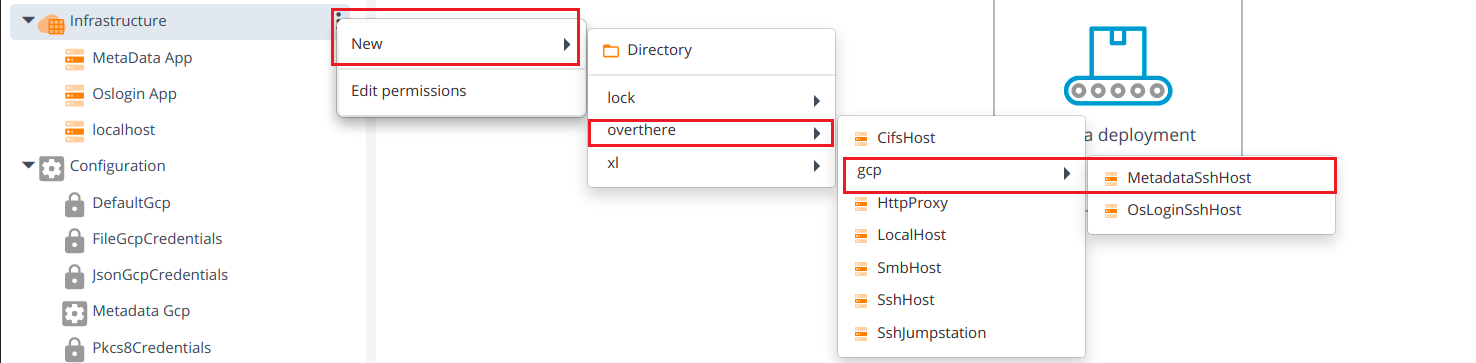
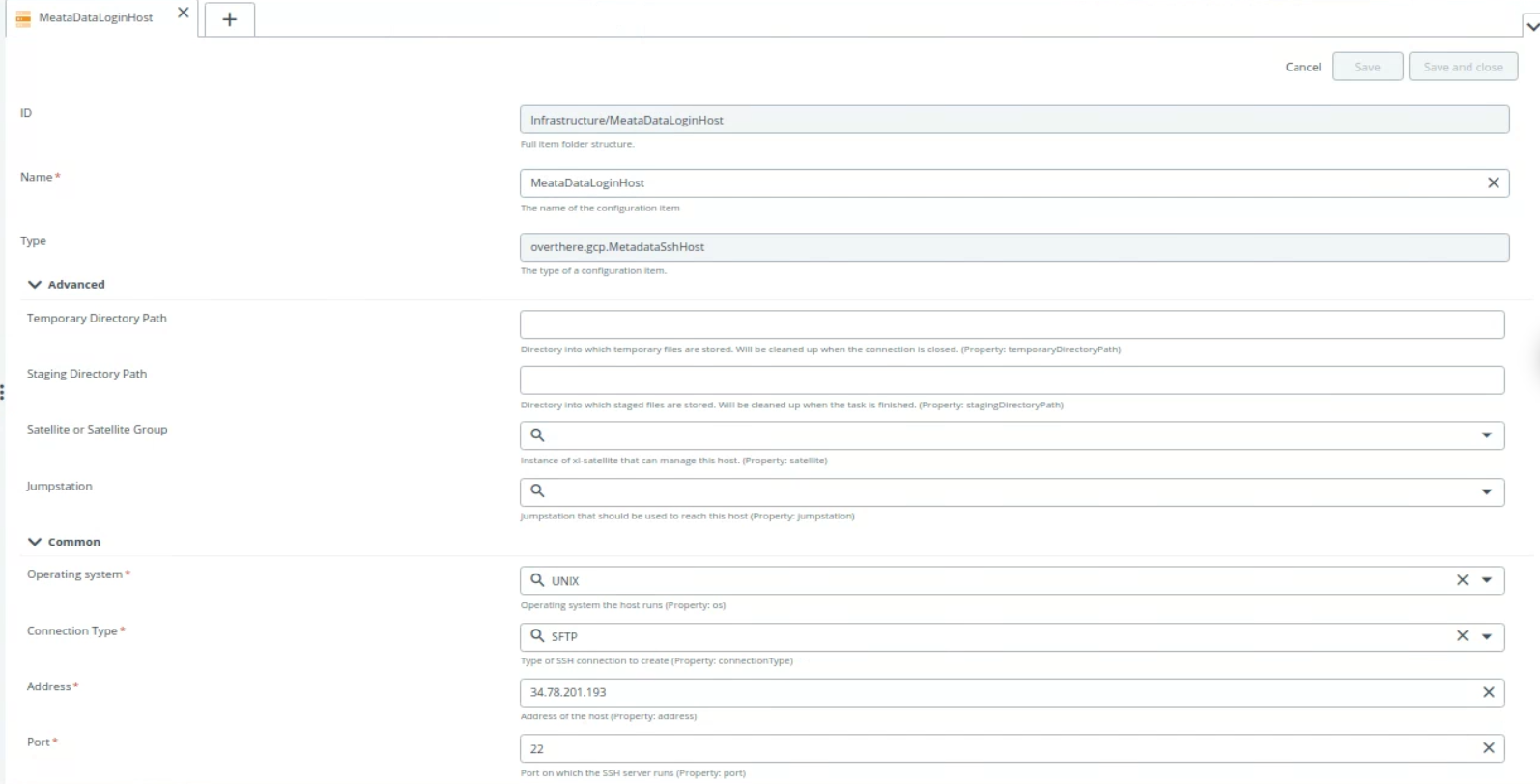
- Create OsLoginSshHost and MetadataSshHost Cis from infrastructures, See create an infrastructure to know more information.
8.1 To create an OsLoginSshHost and MetadataSshHost hover over the Infrastructure, click then select New > overthere > gcp > OsLoginSshHost or MetadataSshHost under the Infrastructure.
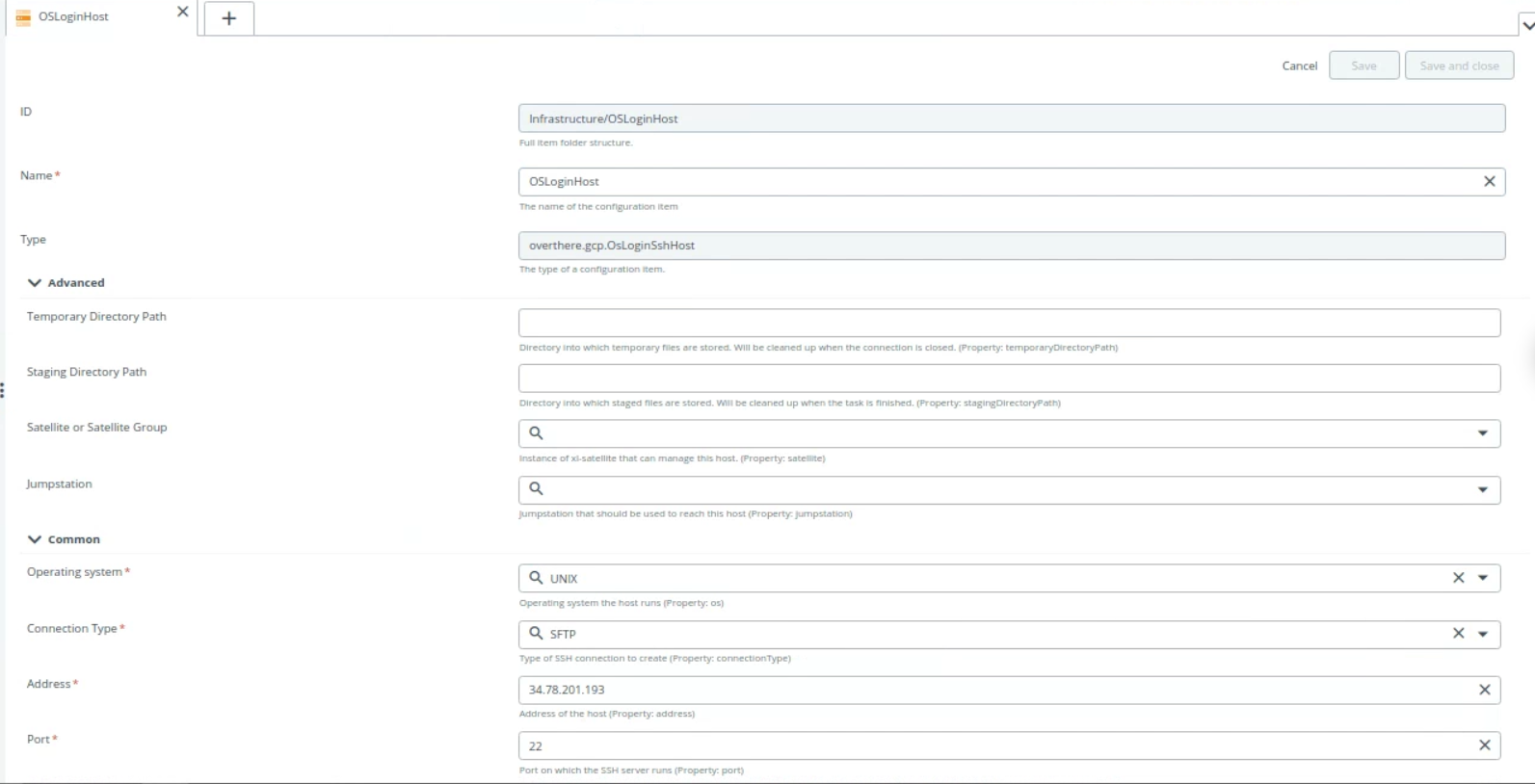
Provide the following values:
- Operating system
- Connection Type
- Address
- Port
- Credentials o Select one of the credentials from steps 2 to 5 o Select the credential created in step 6 for metadata.
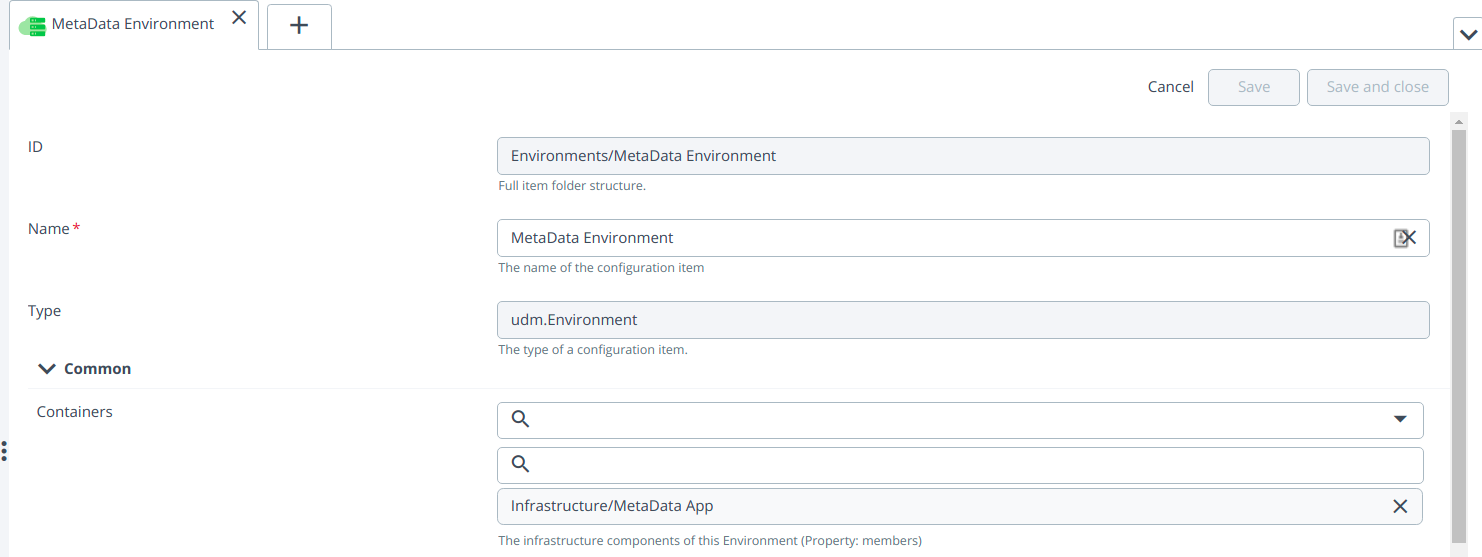
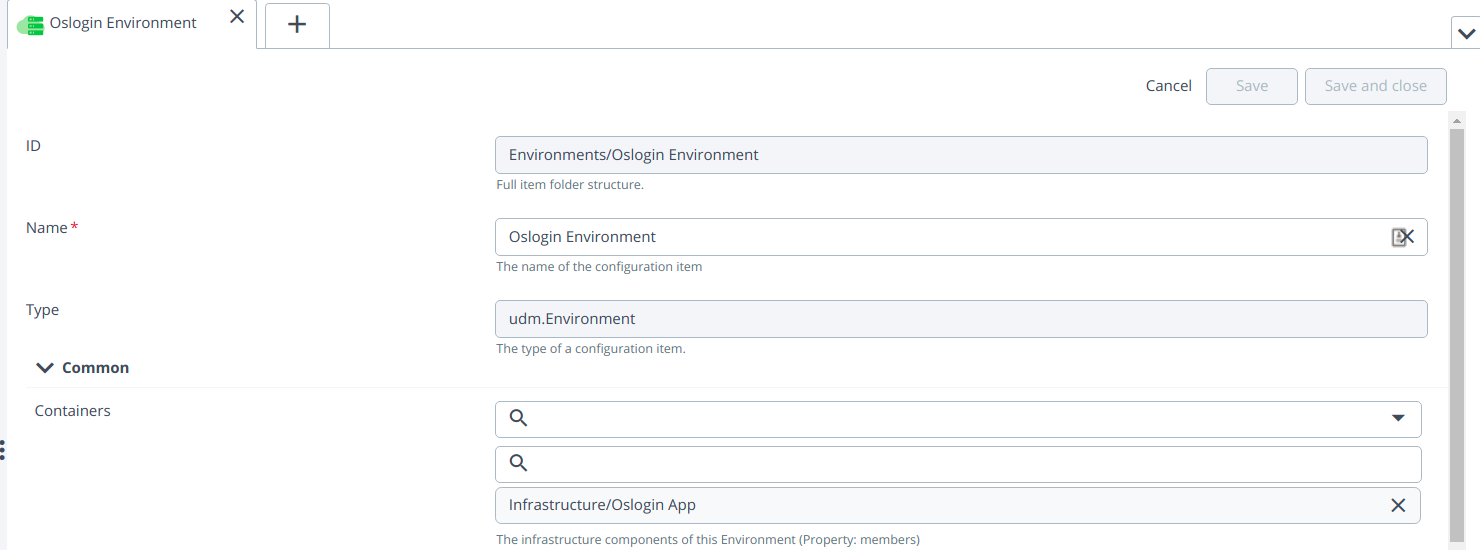
- Create two environment Metadata and oslogin and add the MetadataSshHost to MetaData environment and osLoginSshHost to oslogin environment respectively. See create an environment to know more information.
- Create a cmd application or create and add file type to the cmd application. see create an application for more information.
or
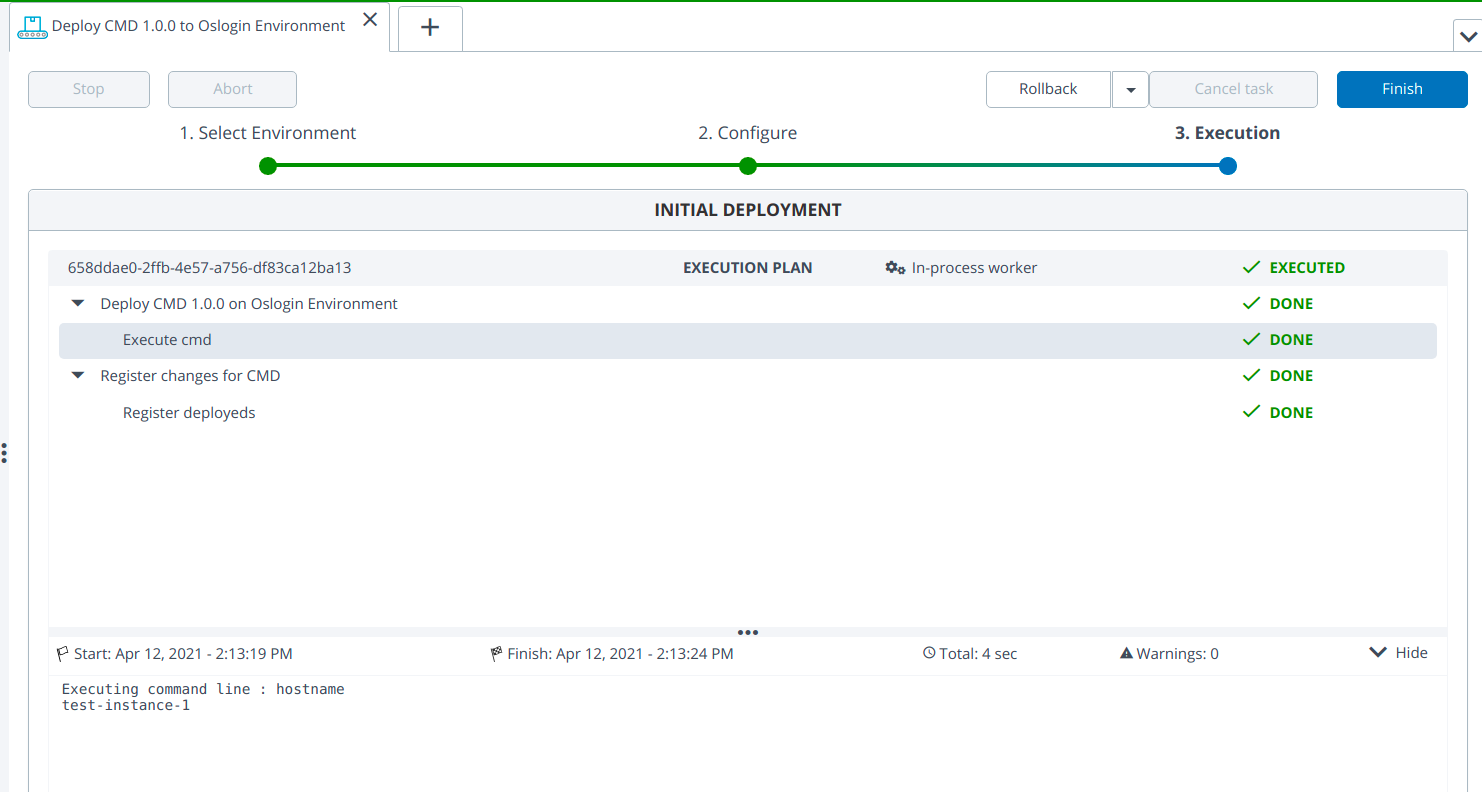
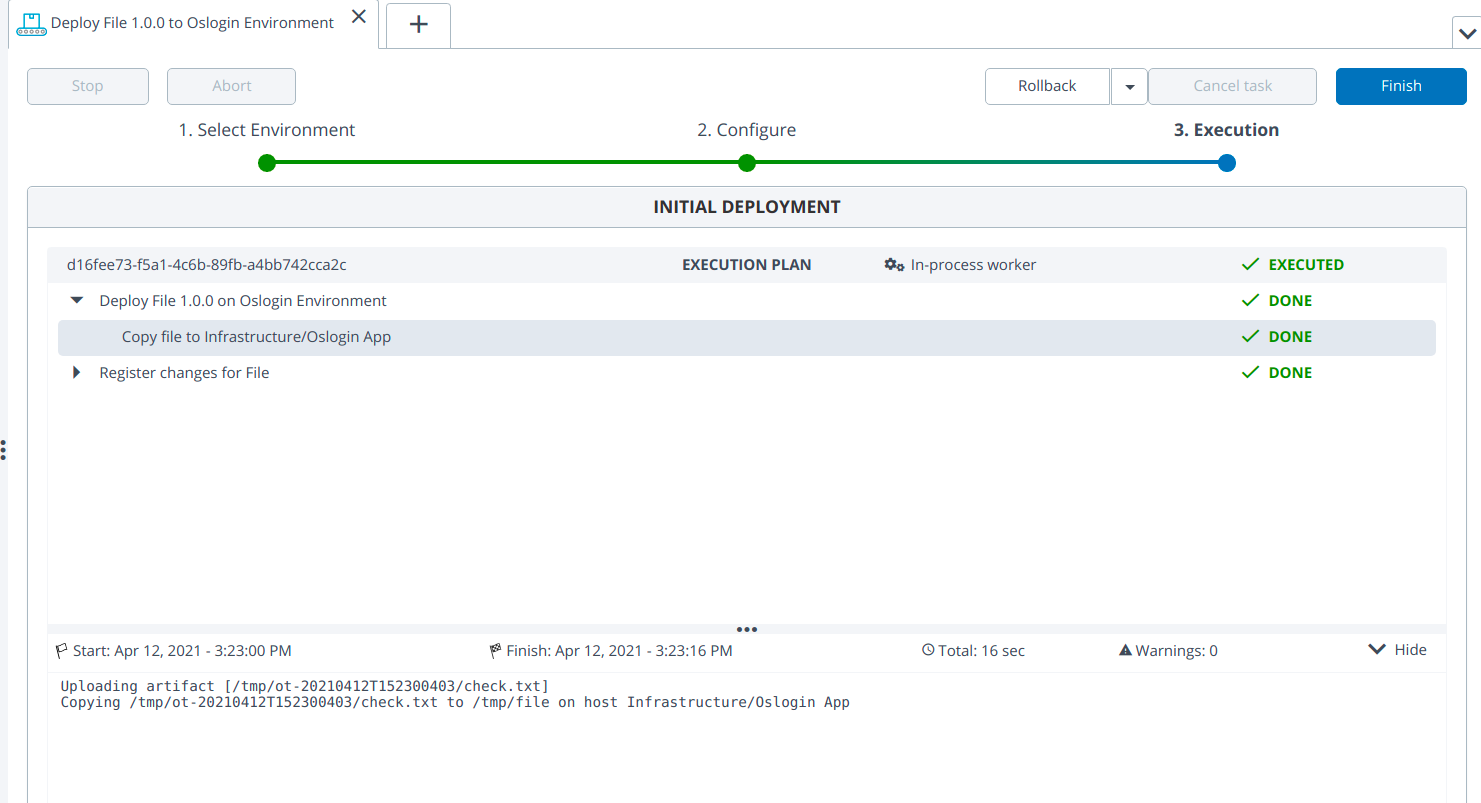
- Deploy the cmd/File type application to the oslogin environment using the following credentials:
- DefaultGcpCredentials
- ServiceAccountFileGcpCredentials
- ServiceAccountJsonGcpCredentials
- ServiceAccountPkcs8GcpCredentials
- ServiceAccountTokenGcpCredentials
Note: File should be copied in case of file type deployment.
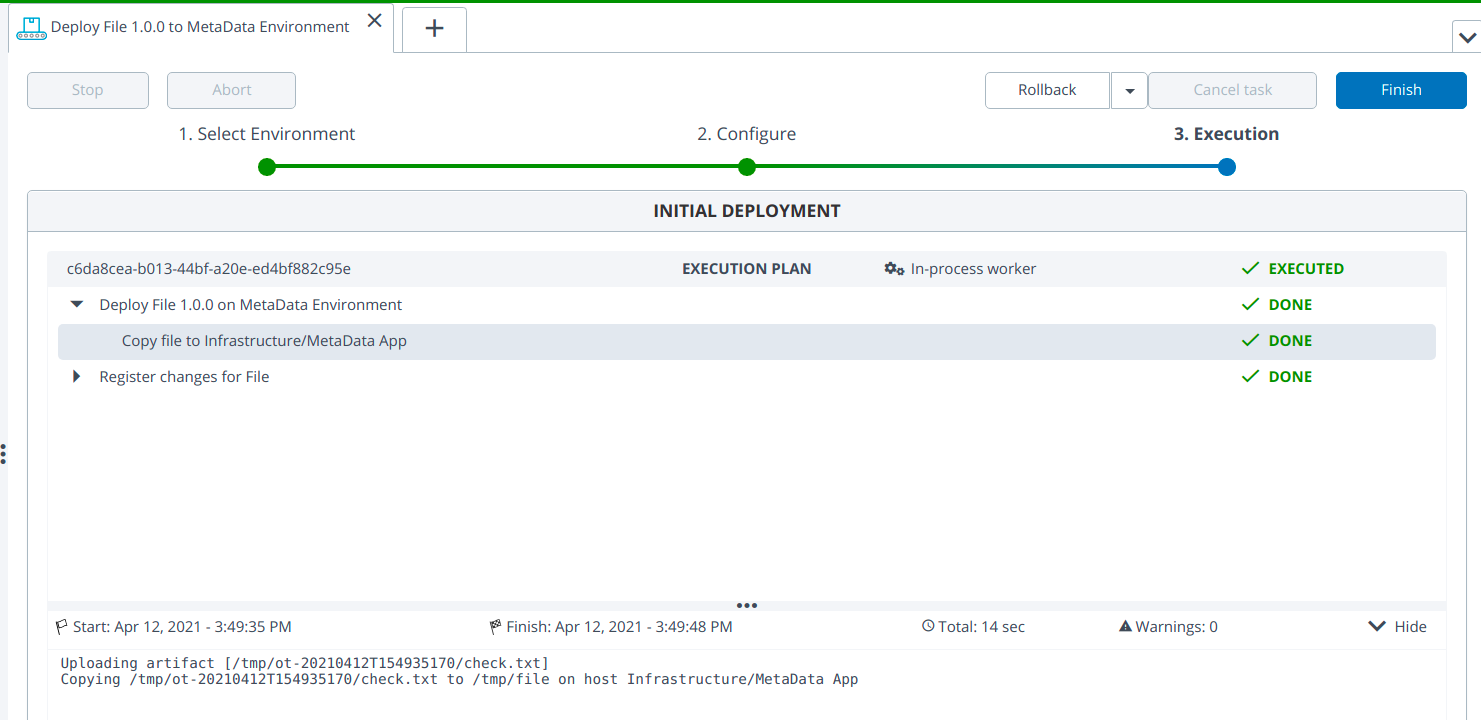
- Deploy the cmd/File type application to the Metadata environment by specifying any one of the following credentials at a time in MetadataSshKeysProvider:
- DefaultGcpCredentials
- ServiceAccountFileGcpCredentials
- ServiceAccountJsonGcpCredentials
- ServiceAccountPkcs8GcpCredentials
- ServiceAccountTokenGcpCredentials
Note: File should be copied in case of file type deployment.
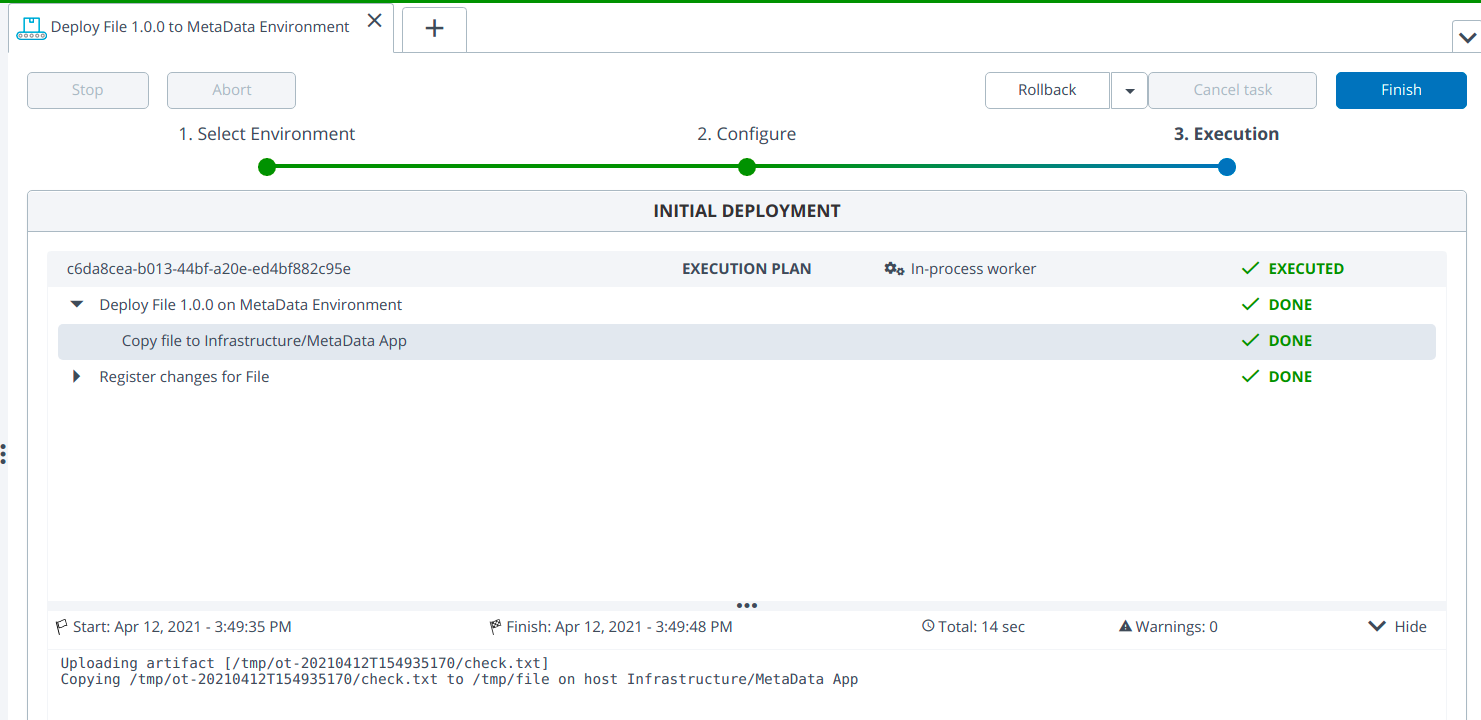
-
Verify the SCP and SFTP supported connections by setting SCP and SFTP in below infrastructure CIs:
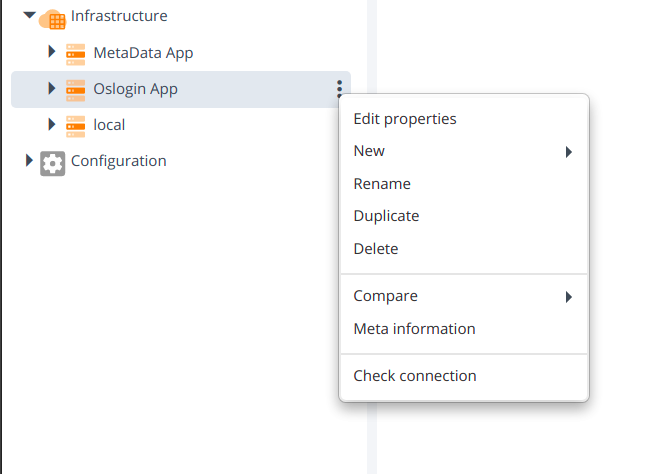
- Check oslogin connection by setting SCP and SFTP.
- Check metadata connection by setting SCP and SFTP.
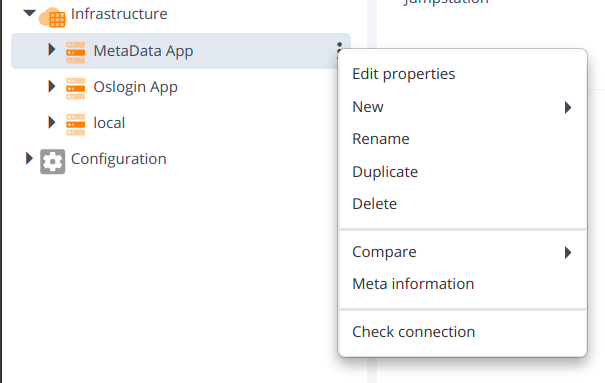
Connection should be successful with SCP and SFTP on oslogin and metadata infrastructure CIs.